You need to prepare packet tracer file
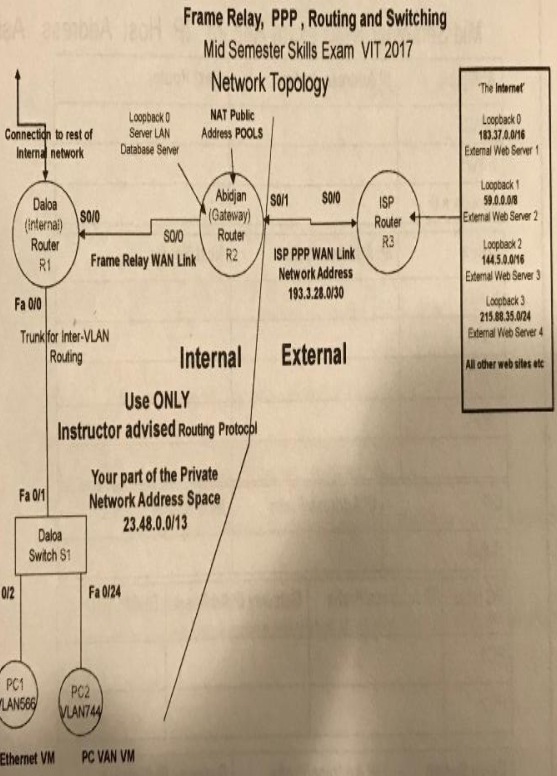
attached pdf contains topology and required configurations and assigned ip address.
In packet tacer file you need to include banner, router and switches.
1. VLSM Design
a) As first task it is important to get your addressing scheme correct and documented
Design IP VLSM Addressing Scheme, using this part 23.54.0..0/14 of Corporate Network space with:
- VLAN 566 Horses 2000 hosts
- VLAN 744 Sheep 600 hosts
- VLAN 819 Cattle 120 hosts
- Abidjan Database Server LAN looprpack 0.50 hosts
- VLAN 1 6 hosts,
- Internal Serial 2 hosts
b) You can use a VLSM calculator
c) Record VLSM Subset Addresses
2. On each router, ensure router config - register is set to 0 x 2142: router(config)*config-register 0 x 2142
3. Do not configure enable passwords OR line console passwords on router and switches, unless specified by the task.
4. Cable connection
a) Conned Dalos router to switch port Fa 0/1
b) Check routes are connected via serial links, refer to page 4
c) Connect PC1 to Fa 0/2 using the patch panel, connect PC2 to Fa 0/24 using the VAN
5. Helpful Configurations
a) Configure the line console on each router and switch as shown below
line console 0
logging synchonous (stops system messages overwriting your typing) exces-timeout 00 (ensure you do not return to user executive mode)
b) Turn off DNS (Domain Name service)
no ip domain lookup (ensure if you miss-type a command the router will not try to resolve the command as a URL web address)
6. Message of the Day (MOTO) Configuration
Configure a MOTO ensure you record your name and student id, on all routers and switches, is shown below:
banner mold &
Welcome to
< Your Family Name>
&
7. Switch configuration
b) Check the switch is clan, if NOT then:
i)Delete the vlan dat file to remove old VLANs from the switch, use -delete vlan.dat
ii) Use - erase startup-cofig then reload
c) Create VLAN see Horses, VLAN 744 sheep, VLAN 819 cattle
d) Configure Fa 0/1 as a trunk point
e) Configure as access ports, only VLAN 566 ports 2,3 and VLAN 744 port 24
f) Switch management - configure an ip address on interface VLAN 1 and configure a default gateways, refer to page 7
g) configure enable password cisco and line vty with password cisco and login so each switch can be configured via telnet
h) Configure Port security, VLAN 566, mac address sticky on ports 2,3 max 2, with violation shutdown
i) Configure a stabc mac address, VLAN 744 on fe 0/24 to the MAC address of PC2
8. Trouble Shooting VLANs
a) To check VLANs created, use -show vlan brief
9. Trouble Port security
a) To check port security is enabled, use -show port security
b) A table will be displayed showing the security status of the switch ports
10. Network IP Address Configuration
a) Configure All The router interfaces and any loopbacks with ip address.
b) Daloa Router
i) Inter-VLAN Routing Configuration
- Configure inter-VLAN Routing on Fa 0/1
- Create separate sub-interfaces for VLANs 1, 566 and 744
- Assign each sub-interface with an ip address
- Configure helper ip address for DHCP
c) Abidjan Router
it NAT Configuration
- Create separate NAT Pools and ACLs for VLANs' 1, 566 744
- Overload each NAT pool
ii) DHCP Configuration
- Create separate NAT Pools and ACLs for VLANs' 1, 566, 744
- Overload each NAT pool
- Exclude the first four IP addresses
d1 PC Configuration
i) Configure PCI and PC1 to obtain IP address automatically
11. Trouble Shooting trunking - between switch and Router
a) To check Trunking is activated, on switchs(es) use - show interface trunk.
b) Check correct interface has been configured for trunking
12. Trouble Shooting DHCP
a) Use debug ip dhcp server events on ALidjan Router, to view the DHCP process
b) Open DOS CMD windows on PC1 and PC2 - ipconfig/release then ipconfig /renew c) Addresses obtained? NO Check router configuration.
Use - show ip dhcp pool, show ip dhcp binding, show run
13. trouble shooting Point-to-point single Link testing
a) This test is to check that each individual link in the network is working
b) Ping (command)- ensure you can ping from one end to each link to the other:
- PC to Route in same subnode/VLAN /network
- PC to PC in same subnet/VLAN network
- Router to each direct neighbor Router over a serial link
c) Link Not working? Common problems:
- Physical connection not made
- The clock rate is not configured on DEC interface of a serial link
- An incorrect IP address or subnet mask is configured on one interface of a link
- The interface is shutdown
14. Trouble shooting Inter-VLAn Routing test
a) This test to check inter-VLAN routing is working
b) Ping PC1 - VLAn 566 to PC2- VLAN 744
15. Trouble shooting telnet to switch
a) To check you lan telnet to switch
b) from PC1 DOS command window - telnet to the switch
c) Common problems:
- Switch Vlan 1 interface shutdown
-switch has no default gateway IP address
- Switch line vty not configured with login and password
- Inter- VLAN routing failure
16. Routing protocol configuration
a) Daloa
- 08PF using wildcard for each subnet
- Configure passive interface as appropriate to avoid sending unnecessary routing information
b) Abidjan
- 08PF using wildcard for each subnet
- configure passive interface as appropriate to avoid sending unnecessary routing information
b) Abidjan
- 08PF using wildcards for each subnet
- Do not advertise the external network address
- Configure passive interface as appropriate to avoid sending routing information
- Configure default route to ISP Router
- Advertise default rote to dalocs Router
c) ISP Router
- Do not configure 08PF
- Only configure a static route to your public NAT Pool address
- Configure loopbacks for Web Servers (if you are using packet tracer may need to use server devices)
17. Trouble shooting 08Pf neighbor Adjacency
a) verify that the routers have formed an adjacency with each other, use above ip neighbor
b) Adjacency NOT formed? If an adjacency has not formed it could be due to:
i) Subnet marks on each end of link do not match
ii) the directly connected subnet is not included in the network statements
c) Other trouble shooting commands show ip protocols debug ip ospf events
18. Trouble shooting Routing presence of subnets
a) Internal Routers
- Use show ip route to display the routing table on each router:
- check all the subnets are present
-check there is a default route
b) I8P Router
- use show ip route to display the routing table:
- check there is static route back to your public NAT Pool Address
c) Common problems:
- Routing protocol is not advertising a subnet
- An interface is down
- Static or default route not configured
19. Trouble Shooting Internal Privals End-to-End Path testing
a) This test is to check that the internal routing static and dynamic is working
b) Use debug ip icmp on Abidjan router to check ping request arrives
c) Ping from PC Hosts in VLAN 590 and VLAN 744 to Database server on Abidjan
d) Use trace route to pin point problems
e) Internal Private End-to-End Path test failed? Common Problems:
- Default gateway IP address not configured on a PC.
- PC connected to incorrect interface
- subnet missing from routing table
- Default route not advertised
20. Trouble Shooting NAT - Internal private to external Public End-to-End testing
a) This test is to check that NAT is working - that the private IP address is being translated to public IP address
b) Use debug ip nat on abdjan to view the NAT translations
c) Use debug ip icmp on ISP router to check ping request arrives
d) Ping from PC Hosts in VLAN 566 and VLAN 744 to the internet - pick an External web server
c) NAT filled? - Common problems:
- ACL and Pool names are case sensitive, check names are correct
- ACL incorrectly configured
- NAT pool incorrectly configured
- Binding of ACL to NAT pool incorrectly or not configured
- inside and outside interface incorrectly or not configured
- On ISP static rote is not pointing to NAT pool
f) Useful commands, use - show ip nat translations, debug ip nat
31. Creating and configuring NAMED Access lists
a) Refer Lab Exercise on Access Control Lists
b) the Notepad to create your ACLs, note ACL are case sensitive eg. Aachivain 556 and acivian 565 are different acts
c) identify each requirement then configure an ACL rule for each requirement.
d) Create a named access list in notepad, considered the ordering of the rules, use the following templates:
!ACL for VLAN an Router
!Deletes previous version of access list
no Ip access list extend ACL VLAN
| insert Latest version of access list
ip access - list ended ACLVLAN
I For most situations this should be the last rule ie permit all other access to " the internet" permit ip any any
e) combine ACL rules as required to form your access list, carefully consider the order in which the rules should be arranged
f) Paste ACL from notepad into router (router must be in global configuration mode)
g) Configure ACL on correct interface
32. Trouble shooting Access lists
It Is importing to verify that the ACL rules actually work as intended, refer to the steps below:
1. use show access- list
If all rules bested go to 5
Else identify which rule you want to test
2. Use clear access-list counters
Clear any counts against the rules
3. Go to PC in VIAN perform test eg. Ping, telnet, Browser etc to trigger a match with the identified rule
4. Use show access lists
Was the identifies rule matched?
Yes - rule action correct, Repeat process go to 1
No Debug
- was another rule matched?
- Where no rules matched?
- Check syntax and order of rules - make changes - repeat process go to 1
- Check syntax and order of rules - make changes - repeat process go to 1
5 Trouble shooting completed
Attachment:- Exam.rar