Introduction
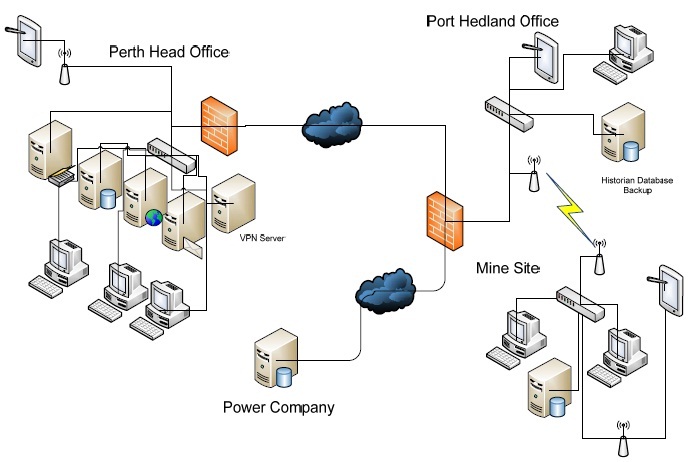
“Big Red Rocks” (BRR) mining company is based and operates in Western Australia. They are mainly an iron ore miner, but they also produce electricity through tidal power to support their crushing operations, with any excess power sold back to power grid through the electricity market. BRR maintains the head office in Perth, and the site office in Port Hedland. There is also a control system network operated at their crushing plant outside of Port Hedland. There is a need for database information from the crusher site to be sent to Perth for accounting and other purposes.
BRR has been informed by CERT Australia that some of their internal documents have been found on external third party websites, and that they have important security issues which have to to be rectified. You are the network security consultant who has been hired to advise on issues present in the present architecture and associated network security issues.
Following hardware and software is in operation at each site:
Perth Head Office
• 200 client desktop PCs running Windows Vista
• Web server (external) running Apache on Redhat Linux
• MS Exchange Server on Windows Server 2008
• 802.11 wireless using WPA TKIP
• Executives have iPads to access the internal network
• Connection between Head Office and PH Site over Telco private WAN
• External Access is via VPN (PPTP) user name and password
• There is an AV server
Port Hedland Office
• Runs 20 PCs with Windows Vista
• Authentication to ADS over the WAN link to Perth
• Connected to mine site via 802.11 wireless (WPA TKIP)
Mining Site
• No ADS – all PCs belong to workgroup
• Connection to PH Site Office via 802.11g point to point link (WPA TKIP)
• 10 PCs running Windows Vista in office
• 5 PCs running Windows NT in the control room (NOTE: This cannot be changed as the SCADA software will not run on the newer OS)
• There are no individual logons or passwords on the control room PCs (Usernames and passwords cannot be implemented as this is an operational issue)
• SCADA engineers remotely connect to the mine site through a VPN Server PPTP Other information:
• The network security policy has not been updated since 2005
• There is no patching regime
• See network diagram shown below (Note: this may be out of date but is the most current we can find)
• The VPN at the Head Office and the VPN at the mine site are not connected
Tasks:
You are required to produce the following deliverables as part of your contract:
1. A list of the issues with BRRs network as it currently stands. The list will describe the vulnerabilities associated with each issue
2. Treatment recommendations to address the identified issues in BRRs networks
3. A detailed network diagram which creates a more secure network for BRRs operations
4. Updated network security policies which take into consideration current issues and hardware
The report should be set out in the following manner:
• 11 point Times New Roman
• 1.5 line spaced
• Margins set to 2.5 cm
• Justification: block justified
• Footer: Should contain your ECU StudentID and Full Name (8 point type) and a Page number
• The report should contain an index and have appropriate headings and sub headings.
• The style of the report is a business report and as such it is expected that you present a professional report in both format and style.
• Your report should not exceed 30 pages in total length
All sources of references must be cited (in text citation) and listed (end reference list). For details about referencing and the required format, please refer to the ECU Referencing Guide, which can be found from the following URL: http://www.ecu.edu.au/centres/library-services/workshopsand-
training/referencing/related-content/downloads/refguide.pdf
Deliverable
Network Diagram
• Complete network diagram detailing new architecture
• IP addresses and other architecture detailed
Network Security Policy
• Policy not procedure
• Covers all relevant devices and technologies and is relevant to BRR