I. OUTLINE
This Case Study will require you to
1) Build a small network using three switches and one router
2) One switch will run as a distribution layer switch, the other two will run as access layer switches
3) A router will be connected to the distribution layer switch using 802.1Q trunking to route between subnets
4) The switches will be connected with two Ethernet links using Ether-channel bonding
5) The distribution layer switch will be con?gured as the STP root bridge
II. CASE STUDY DETAILS
Your Lab Supervisor will provide your group with your:
- � Company/orgnaisation name
- � Allocated network address information
- � Subnetting requirements for four LANs to operate within your organisation
- � VLAN numbers and VLAN names for each of the four LANs
- � Network Management VLAN to use in your network
These details will be provided once you have registered your group within ESP and provided those details to your supervisor.
III. LOGICAL NETWORK TOPOLOGY
The logical topology for the organisations network is depicted in the ?gure below. Your organisation consists of four LANs which will each be connected to a single router to route traf?c between subnets.
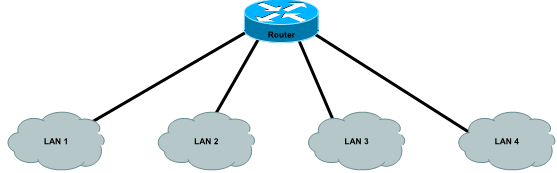
IV. NETWORK ADDRESSING
Your Lab Supervisor has provided you with a network address (and subnet mask) and subnetting requirements for each of your four LANs. When subnetting your network to accomodate the required hosts for each of your four LANs, you must:
- � Ensure that you have enough subnets to address the entire network
- � Allocate a subnet for the management network (switches and routers) large enough to cover network growth of double the current ammount of infrastructure
- � Subnet optimally such that the largest number of IP addresses within your allocated network remain for future expansion
In your ?nal report, you must explain your subnetting process and show your calculations.
V. SWITCH PORT ALLOCATION
You have been provided with ?ve VLAN identi?ers for your network, one for each of your four LANs and one for your management VLAN. You have been provided with appropriate names for the VLANs covering the subnets. The physical topology of your network must match the network diagram below.
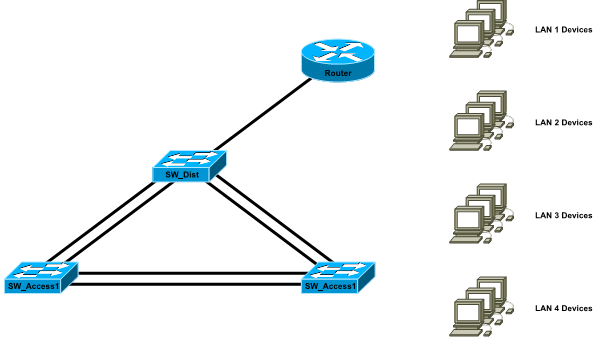
For each port on the four network devices, you must nominate:
- � Whether it will operate in access or trunking mode
- � Which VLANs are allocated to which ports, and on which switches
- � Which ports will be disabled
In your ?nal report, you must explain your decision process for switch port allocation.
VI. BASIC DEVICE CONFIGURATION
You are required to con?gure all switches and routers with the following information:
- � Device names
- � Message of the Day
- � Interface descriptions
- � Console and Enable passwords
- � ssh Access
- � All router interfaces are to have the lowest usable IP address of their allocated subnet
Further, all switches should be con?gured such that:
- � Unallocated ports are disabled
- � Appropriate switch-port security is con?gured
In your report you will need to justify your switchport security decisions and con?gurations.
VII. ADVANCED NETWORK CONFIGURATION
You will be required to con?gure 802.1Q trunking connections between the switches. Each switch will be connected to another switch via two trunking connections where the second connection is used for redundancy purposes.
You will be required to con?gure your network Spanning Tree Protocol to PVST+ and to ensure that the distribution layer switch is the Root Bridge.
VIII. ETHERCHANNEL BUNDLING
Network traf?c has grown since you ?rst built your network. The Ethernet trunking channels are no longer capable of carrying the offered load on their own. A decision has been made to change the redundant trunking connections between each switch into a bundled EtherChannel to double the maximumum throughput.
You must recon?gure your network such that the two links connecting the switches now form an EtherChannel. You must ensure that the distribution layer switch remains the Root Bridge for the Spanning Tree Protocol.
A. Testing
As part of the Case Study, you need to devise and document an appropriate testing regime to ensure that all the following conditions are met:
1) The nominate level of switchport security is functional
2) Full interconnectivity exists between all hosts in all LANs and the management VLAN
3) The redundant trunking links are functional in the event of failure of the primary links
4) The correct switch is con?gured as the PVST+ Root Bridge
5) EtherChannel bundling is correctly con?gured, the channel bandwidth is indeed doubled, and that the root bridge remains properly con?gured
6) ssh access to all network devices is functional
IX. ASSESSMENT ITEMS
The Case Study submission will consist of two components:
1) Prepare a report
2) A video presentation
A. Report Contents
You are required to produce a report that contains the following information.
Subnetting Discussion
A discussion of your subnetting approach, your calculations for each subnet, why particular subnet masks were chosen and how you allocated the subnets to individual networks
Network Drawing
A complete network drawing detailing allocation of addressing information for all relevant hosts and devices. This documentation must include port and VLAN allocation for all devices
Device Con?guration Summary
Tables containing the device information that is not included within the network drawing, including:
- � Hostname information
- � Console, enable and ssh passwords
- � Assigned interface descriptions and the MOTD
- � Port security summary
Design Discussion
Discussion of your design and decision making processes and reasoning. These discussions must include:
- � Swithport allocation reasoning
- � Port security reasoning and design
- � Spanning Tree implementation details to de?ne the root bridge
- � Planning for redundancy and EtherChannel considerations and deployment
Device Output
A copy of the output of the following commands on all devices:
show version
show run
sh ip int brief
sh ip route (routers only)
sh vlan brief (switches only)
sh interface trunk (switches only)
Testing Procedure
An outline of how you built your network and an overview of your testing to verify the complete functionality of your network