Practical: Access Control Lists
Topology Diagram
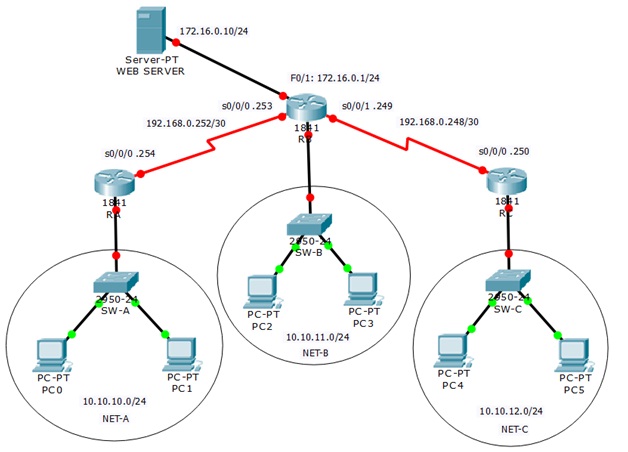
Addressing Table
|
Device
|
Interface
|
IP Address
|
Subnet Mask
|
Default Gateway
|
|
RA
|
F0/0
|
10.10.10.1
|
255.255.255.0
|
N/A
|
|
F0/1
|
None
|
Not connected
|
N/A
|
|
S0/0/0
|
192.168.0.254
|
255.255.255.252
|
N/A
|
|
RB
|
F0/0
|
10.10.11.1
|
255.255.255.0
|
N/A
|
|
F0/1
|
172.16.0.10
|
255.255.255.0
|
N/A
|
|
S0/0/0
|
192.168.0.253
|
255.255.255.252
|
N/A
|
|
S0/0/1
|
192.168.0.249
|
255.255.255.252
|
N/A
|
|
RC
|
F0/0
|
10.10.12.1
|
255.255.255.0
|
N/A
|
|
S0/0/0
|
192.168.0.250
|
255.255.255.252
|
N/A
|
|
PC0
|
NIC
|
10.10.10.2
|
255.255.255.0
|
10.10.10.1
|
Learning Objectives
Upon completion of this lab, you will be able to:
- Design named standard and named extended ACLs.
- Apply named standard and named extended ACLs.
- Test named standard and named extended ACLs.
- Troubleshoot named standard and named extended ACLs.
Scenario
In this lab, you will learn how to configure basic network security using Access Control Lists. You will apply both standard and extended ACLs.
Task 1: Prepare the Network
Step 1: Create a network that is similar to the one in the topology diagram.
Note:This lab was developed and tested using 1841 routers.
Task 2: Perform Basic Router Configurations
Configure the RA, RB, RC routers and switches according to the following guidelines(bold lines are mandatory, normal lines are optional):
- Configure the router hostname to match the topology diagram.
- Disable DNS lookup.
- Configure an EXEC mode password of class.
- Configure a message-of-the-day banner.
- Configure a password of cisco for console connections.
- Configure a password for VTY connections.
- Configure IP addresses and masks on all devices.
- Enable OSPF area 0 with a process ID of 1 on all routers for all networks.
- Verify full IP connectivity using the ping command.
Task 3: Configuring a Standard ACL
Standard ACLs can filter traffic based on source IP address only. A typical best practice is to configure a standard ACL as close to the destination as possible.In this task, you are configuring a standard ACL. The ACL is designed to block traffic from NET-A to access NET-B.
Which router should we create the access-control list?
Step 1: Create the ACL on the router.
In global configuration mode, create a standard named ACL called A_TO_B_DENY.
R(config)#ip access-list standard A_TO_B_DENY
In standard ACL configuration mode, add a statement that denies any packets with a source address of NET-Aand prints a message to the console for each matched packet.
R(config-std-nacl)#deny NET-A-IPWILD-CARD log
Permit all other traffic.
R(config-std-nacl)#permit any
Step 2: Apply the ACL.
Which interface should we apply the ACL and for which direction?
Apply the ACL A_TO_B_DENY
R(config)#interface int_name
R(config-if)#ip access-group A_TO_B_DENY direction (IN/OUT)
R(config-if)#end
R#copy run start
Step 3: Test the ACL.
Before testing the ACL, make sure that the console of the router is visible. This will allow you to see the access list log messages when the packet is denied.
Test the ACL by pinging any PC in NET-B from NET-A. Since the ACL is designed to block traffic with source addresses from NET-A network, the ping should fail.
What have you seen the following message on the router console?
In privileged EXEC mode on the router, issue the show access-lists command. You see output similar to the following. Each line of an ACL has an associated counter showing how many packets have matched the rule.
Standard IP access list A_TO_B_DENY
10 deny 192.168.11.0, wildcard bits 0.0.0.255 log (5 matches)
20 permit any (25 matches)
The purpose of this ACL was to block hosts from NET-A network. Any other hosts, such as those on the NET-C network should be allowed access to NET-B. Conduct another test to ensure that this traffic is not blocked.
Task 4: Configuring an Extended ACL
When greater granularity is required, you should use an extended ACL. Extended ACLs can filter traffic based on more than just source address. Extended ACLs can filter on protocol, source, and destination IP addresses, and source and destination port numbers.
An additional policy for this network states that devices from NET-A and NET-C are only permitted to access the WEB SERVER but other hosts. Because this requirement needs to enforce both source and destination, an extended ACL is needed.
In this task, you are configuring an extended ACL on RA and RC that permits traffic originating from NET-A and NET-C to the WEB SERVER while blocks the traffics to access other hosts in the WEB SERVER network. A typical best practice for applying extended ACLs is to place them as close to the source as possible. So which interfaces should the ACLs be placed?
Before beginning, verify that you can ping the WEB SERVER from NET-A and NET-C.
Step 1: Configure a named extended ACL on RA.
In global configuration mode, create a named extended ACL called A_TO_WS_ONLY.
RA(config)#ip access-list extended A_TO_WS_ONLY
Notice that the router prompt changes to indicate that you are now in extended ACL configuration mode. From this prompt, add the necessary statements to permit traffic from NET-A to the WEB SERVER port 80 and block traffic to other hosts in the WEB SERVER network. Use the host keyword when defining the destination.
RA(config-ext-nacl)#permittcpNET-A-IPWILD-CARD host WEB-SERVER-IP eq www
RA(config-ext-nacl)#permiticmpNET-A-IPWILD-CARD host WEB-SERVER-IP
RA(config-ext-nacl)#denyip NET-A-IPWILD-CARDWEB-SERVER-NET WILD-CARD
Recall that the implicit "deny all" blocks all other traffic without the additional permit statement. Add the permit statement to ensure that other traffic is not blocked.
R1(config-ext-nacl)#permit ip any any
Step 2: Apply the ACL.
Extended ACLs are typically placed close to the source. Which interface should we place the ACL on and which direction should we use?
RA(config)#interfaceint-name
RA(config-if)#ipaccess-group A_TO_WS_ONLYdirection
RA(config-if)#end
RA#copy run start
Step 3: Test the ACL.
From NET-A, ping the WEB SERVER.These pings should go through. If we ping any other hosts including the router RB F0/1 interface, the pings should fail.
Step 4:Create and apply an extended ACL for router RC and verify it.
Issue the show ip access-liston RA and RC after pinging to see the access lists in active.
Step 5: Restore the ACL to its original configuration.
Remove the ACL from the interfaces.
R(config)#interface interface-name
R3(config-if)#no ip access-group ACL-NAMEapplied-direction
Task 5: Document the Router Configurations
Issue show run command on each router to report the router configurations and paste here
RouterRA
Router RB
Router RC