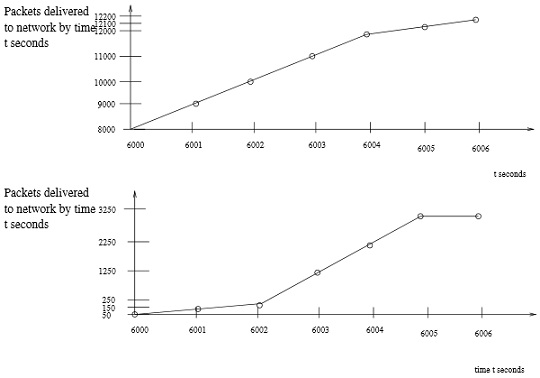
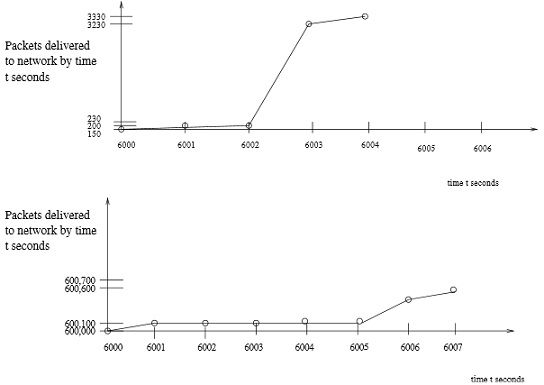
Answer the following problems.
problem 1) Networking community has explored two various approaches for providing different classes of service: integrated services (IntServ) and differentiated services (DiServ). Briefly compare and contrast the two.
problem 2) Why do services with convex utility curves need admission control?
problem 3) Services with convex utility curves are sometimes referred to as inelastic services. Other than admission control, what else might a service administrator do to make sure that users receive sufficient bandwidth to make the service usable?
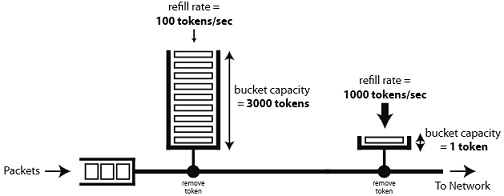
problem 4) Token buckets are often used to make sure that flows entering a QoS-controlled network behave correctly. Consider the figure below showing a flow passing through 2 token buckets before it enters the network.
you are given 4 flow behaviors. Circle those which could have passed through the tandem leaky bucket policer