Information System Security Assignment
Differentiate Following:
1. Threat and Attack
2. Active Attack and Passive Attack
3. Interruption and Interception
4. Virus and Worm
5. Sniffing and Spoofing
6. Phishing and Pharming
7. Substitution and Transposition
8. Symmetric Key and Asymmetrical Key
9. Vigenere Cipher and Vernam Cipher
10. Cryptography and Steganography
EXERCISE:
Note: - Map A-Z with 0-25
1. Do the Encryption using a Caesar Cipher where key K=3. Plain Text: U V PATEL COLLEGE OF ENGINEERING
2. Do the Encryption using a Vigenere Cipher where Key is dollars. Plain Text: the house is being sold tonight Also Do the Decryption process.
3. Do the encryption and decryption using Playfair cipher Plain text: the key is hidden under the door pad Key: guidance
4. Do the Decryption using a Play fair Cipher where Key is COMMING.
Cipher Text: HEXMRXAWLDUMGBSUCAIA
5. Do the Encryption using a Play fair Cipher where Key is CONGRUENCE 179. Plain Text: NUMBER THEORY Also Do the Decryption process.
6. Do the encryption and decryption using Hill Cipher on plain text "CODE"
7. Do the Encryption us ng a Hill Cipher on plain text "GOOD"
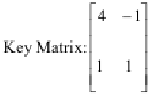
Also Do the Decryption process.