Answer the follwoing problems.
problem 1) Elisa wishes to listen to National Public Radio news over the Internet. She starts her favourite audio player and points it to ra1.streaming.npr.org. Audio player calls gethostbyname() with given name to get IP address of the server. Therefore of the gethostbyname() call, local resolver in Elisa's machine contacts local DNS server to translate the host name into the IP address. The local DNS server performs an iterative lookup. The table below contains the DNS distributed database. A row corresponds to a DNS record. The records are grouped by DNS server.
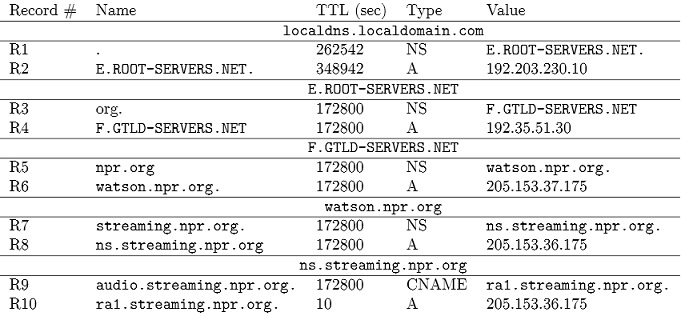
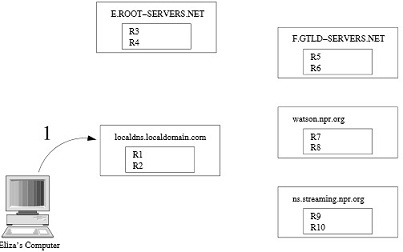
problem 2)a) In the figure below, draw arrows to indicate sequence of queries and responses exchanged among the different machines. Label each arrow with a sequence number and, if the message is a response, indicate which record(s) it contains. To make your sequence as simple as possible, suppose the server includes both the A and NS records when applicable.
b) Eliza repeats her query after two minutes. Demonstrate what happens for this subsequent query.
problem 3) State true or False.
Briefly describe your answers.
i) In CCN, data packets are forwarded using longest prefix match.
ii) Nonce in a CCN interest packet is to prevent replay attacks.
iii) Compared to IP, CCN makes it more difficult to target a particular host with denial of service attack.