problem 1:
a) Express the Shannon-Hartley capacity theorem in terms of Eb/N0 where Eb is the Energy/bit and N0/2 is the psd of white noise. You can use the given identity in your work:
Eb/N0 = (S/N)(W/R)
Where,
S = average modulating signal power
R = bit rate
N = N0.W
b) In the given figure describe the behavior of the 2 modulating schemes at the two circles shown at the same level.
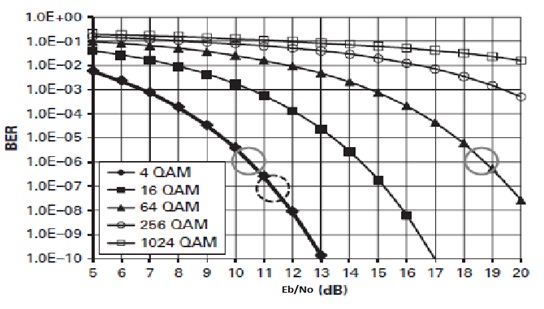
problem 2:
Consider a baseband signal x(t) having a bandwidth of 5 KHz. This signal is modulated to obtain the given signal:
xc (t) = x(t).cos (2.π.fct)
a) prepare the general expression in terms of Fourier Transform for the resulting spectrum of the signal xc(t).
b) Draw the approximate magnitude spectrum of the modulated signal. Show the LSB, USB and the Double-Sideband Bandwidth (WDSB) in your diagram.
problem 3:
a) Recognize the 3 transmitter masks and mention the 3 popular wireless technologies which each of these belong to.
b) Which of the practical signal(s) is (are) in violation of such masks and why?
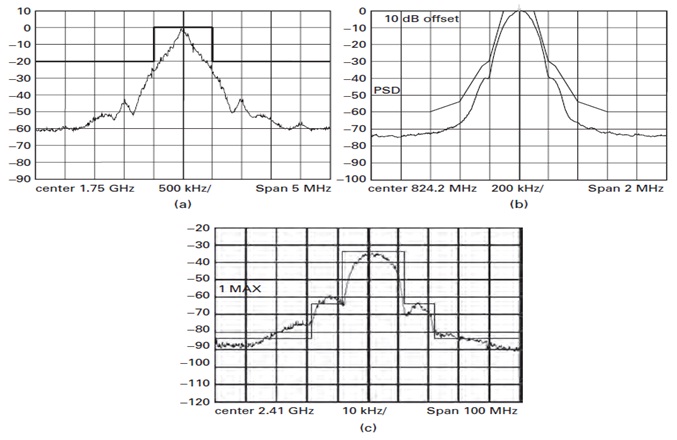
problem 4:
Consider a forward traffic generation method in the IS-95 communication standard as illustrated below:
a) Briefly describe in your own words the purpose of the Convolutional encoder block.
b) Briefly describe in your own words the purpose of the interleaver block.
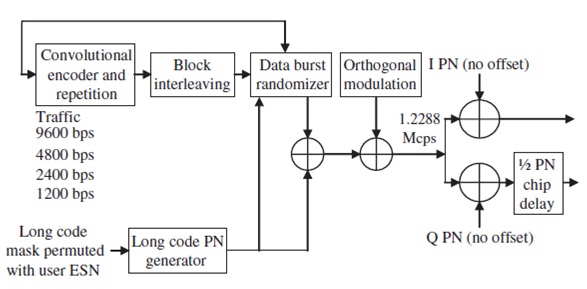
problem 5:
This problem is associated to the system failure part of your study.
a) Briefly describe what is meant by the battery electric vehicle (BEV).
b) What is the Tesla Electric car project?
c) Briefly describe the “Bricking” problem with the battery system of the Tesla produced car.
d) Briefly discuss how the infrastructure needs and the battery problems can make adoption of the battery electric vehicle on mass scale a problem.
e) Please give references employed to extract the information for this problem.
problem 6:
This problem is associated to the futuristic use of ICTs (driverless cars).
a) Briefly discuss the difference among the Google Driverless Car project and that of the University of Harvard’s in the UK from navigation technology employed in the two projects.
b) List at least 4 advantages of the Driverless Car project.
c) Please give references used to extract the information for this problem.
problem 7:
This problem is associated to the case studies part of your course.
a) Consider the Saudi Arabia ICT case study which is part of your Block 3. Describe in your own words the ICT contribution to the national GDP of KSA. Can ICT help diversify the economy away from total dependence on oil and mining in KSA.
b) Briefly discuss how requests for service in remote regions are handled by CITC as per the above case study.
c) Choose a new case study dealing with the utilization of ICTs in resolving different social, cultural and developmental issues either in the Middle East or the developing world. prepare a short paragraph describing why you selected your case study. You must comprise the case study as part of your TMA work.