problem 1) Consider a network with ring topology, link bandwidths of 1000 Mbps, and propagation speed 2×108m/s
(a) What would the circumference of loop require to be to exactly contain one 1500 byte packet, suppose nodes don’t introduce delay?
(b) What would the circumference of the loop require to be to contain at least one 1500 byte packet, if there was a node every 250 m, and each node introduced 32 bits of delay (bit time cost in queue)?
problem 2) Chuck, the ex-student, is given the task of building the new network link technology. Unfortunately, many of his beta-testers complain that their packets get corrupted when using his technology! He tracks out the problem down to time synchronization problems between sender and receiver on link. Perhaps you can help Chuck solve his problems by telling him little about different encoding methods:
For each of these sub-parts, identify whether encoding can have problems with:
A. Long strings of 0s
B. Long strings of 1s
C. Both long strings of 1s or long strings of 0s
D. None of the above
(a) Manchester encoding
(b) NRZ encoding
(c) NRZI encoding
(d) Sketch the digital waveform corresponding to Manchester encoded version of this sequence of 0s and 1s. Following given you the NRZ version.
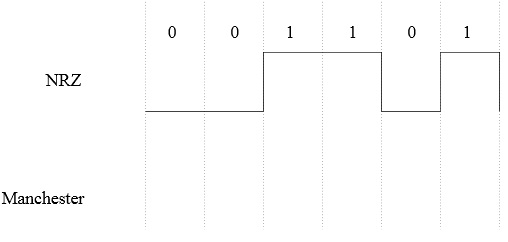
problem 3) For this problem, suppose that ethernet network uses Manchester encoding. Suppose that the hosts on this ethernet network don’t have synchronized clocks. Why does this permit collisions to be detected soon after they occur, without waiting for the CRC at the end of the packet?
problem 4)(a) For the ideal channel of 2.4 GHz bandwidth, what is the maximum channel capacity in bits per second?
(b) For a noisy channel of 2.4 GHz bandwidth and signal-to-noise ratio SN of 1000, what is the maximum channel capacity in bits per second?