Answer the following problems.
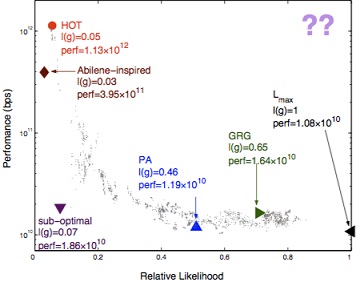
problem 1) prepare down the two reasons that there are not any real-world networks in the top right section of the likelihood-performance plane described in the HOT paper in above diagram.
problem 2) At time t, a TCP connection has congestion window of 4000 bytes. The maximum segment size used by the connection is 1000 bytes. What is the congestion window after it sends out 4 packets and receives ACKs for all of them?
(a) If a connection is in slow-start?
(b) If a connection is in congestion avoidance (AIMD mode)?
problem 3) In congestion avoidance (CA) mode, a TCP sender increases size of its congestion window by one maximum segment size (MSS) each RTT. Assume a TCP implementation does this by increasing its congestion window by Δ every time it receives an ACK, where
Δ - MSS/current window size
Knowing this, how can a greedy TCP receiver get more than its fair share of link bandwidth? (Hint: Remember that sequence number acknowledged by the ACK doesn't refer to a packet, but rather to a byte in the data stream.)