Project - Case Study
I. OUTLINE
This Case Study will require you to
1) Build a small network using three switches and one router
2) One switch will run as a distribution layer switch, the other two will run as access layer switches
3) A router will be connected to the distribution layer switch using 802.1Q trunking to route between subnets
4) The switches will be connected with two Ethernet links using Ether-channel bonding
5) The distribution layer switch will be configured as the STP root bridge
II. CASE STUDY
DETAILS
Your Lab Supervisor will provide your group with your:
- Company/orgnaisation name
- Allocated network address information
- Subnetting requirements for four LANs to operate within your organisation
- VLAN numbers and VLAN names for each of the four LANs
- Network Management VLAN to use in your network
These details will be provided once you have registered your group within ESP and provided those details to your supervisor.
LOGICAL NETWORK TOPOLOGY
The logical topology for the organisations network is depicted in the figure below. Your organization consists of four LANs which will each be connected to a single router to route traffic between subnets.
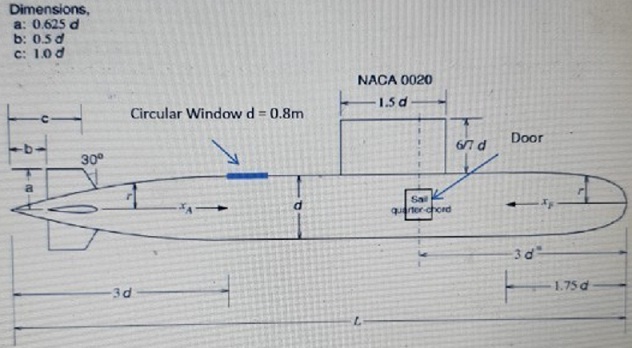
NETWORK ADDRESSING
Ask your staff and get the sub netting requirements for each of your four LANs. When sub netting your network to accommodate the required hosts for each of your four LANs, you must:
- Ensure that you have enough subnets to address the entire network
- Allocate a subnet for the management network (switches and routers) large enough to cover network growth of double the current amount of infrastructure
- Subnet optimally such that the largest number of IP addresses within your allocated network remain for future expansion
In your final report, you must explain your sub netting process and show your calculations.
| Lan 1- Hosts |
Lan 2- Hosts |
Lan 3- Hosts |
Lan 4- Hosts |
| 8000 |
2000 |
500 |
100 |
| 4000 |
1000 |
250 |
58 |
| 2000 |
500 |
100 |
28 |
| 1000 |
250 |
58 |
10 |
| 8000 |
500 |
100 |
28 |
| 8000 |
4000 |
100 |
58 |
| 1000 |
500 |
28 |
10 |
| 500 |
250 |
28 |
10 |
| 250 |
100 |
58 |
28 |
| 2000 |
1000 |
250 |
58 |
| 3000 |
2000 |
500 |
250 |
| 1000 |
500 |
250 |
150 |
V. SWITCH PORT ALLOCATION
You have been provided with five VLAN identifiers for your network, one for each of your four LANs and one for your management VLAN. You have been provided with appropriate names for the VLANs covering the subnets.
The physical topology of your network must match the network diagram below.
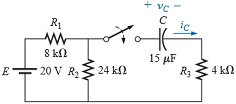
For each port on the four network devices, you must nominate:
- Whether it will operate in access or trucking mode
- Which VLANs are allocated to which ports, and on which switches
- Which ports will be disabled
In your final report, you must explain your decision process for switch port allocation.
VI. BASIC DEVICE CONFIGURATION
You are required to configure all switches and routers with the following information:
- Device names
- Message of the Day - Interface descriptions
- Console and Enable passwords
- ssh Access
- All router interfaces are to have the lowest usable IP address of their allocated subnet
Further, all switches should be configured such that:
- Unallocated ports are disabled
- Appropriate switch-port security is configured
In your report you will need to justify your switch port security decisions and configurations.
VII. ADVANCED NETWORK CONFIGURATION
You will be required to configure 802.1Q trunking connections between the switches. Each switch will be connected to
another switch via two trunking connections where the second connection is used for redundancy purposes.
You will be required to configure your network Spanning Tree Protocol to PVST+ and to ensure that the distribution layer switch is the Root Bridge.
VIII. ETHERCHANNEL BUNDLING
Network traffic has grown since you first built your network. The Ethernet trunking channels are no longer capable of carrying the offered load on their own.A decision has been made to change the redundant trunking connections between each switch into a bundled Ether Channel to double the maximum throughput.
You must reconfigure your network such that the two links connecting the switches now form an Ether Channel. You must ensure that the distribution layer switch remains the Root Bridge for the Spanning Tree Protocol.
Case Study
A. Testing
As part of the Case Study, you need to devise and document an appropriate testing regime to ensure that all the following
conditions are met:
1) The nominate level of switchport security is functional
2) Full interconnectivity exists between all hosts in all LANs and the management VLAN
3) The redundant trunking links are functional in the event of failure of the primary links
4) The correct switch is configured as the PVST+ Root Bridge
5) EtherChannel bundling is correctly configured, the channel bandwidth is indeed doubled, and that the root bridge remains
properly configured
6) ssh access to all network devices is functional
IX. ASSESSMENT ITEMS
The Case Study submission will consist of two components:
1) A report, assessed out of a total of 40 marks and worth 10% of your final mark. All group members will receive the same mark for the report
Attachment:- Case Study.rar