Networking Case Study
Introduction
This case study has been divided into five components.
You are to design a network, research and source appropriate devices justifying choices (feasibility, efficiency, etc.), subnet the network, assign IP addresses to the appropriate devices, and write an executive summary for the project.
You will also be required to prepare proposal to use cloud computing, taking into security, performance and cost.
Scenario
A major Australian data analytics company has asked you to assess and redesign their network. They are opening new branches in Brisbane and Adelaide, which will require new equipment. They have existing contracts and hardware to maintain fibre optic leased line WAN links between sites.
PART 1 - Executive summary
PART 2 - Network diagram
PART 3 - Subnet the network and assign IP addresses to the appropriate devices
PART 4 - Research and source appropriate devices justifying choices (feasibility, efficiency, etc.) with a Weighted Scoring Model (WSM)
PART 5 - Cloud computing proposal
PART 1 - Executive summary
Describe the purpose, scope, and objectives of the project for each of parts 2, 3 and 4. Why is it important to produce a well-designed network diagram? What goals are you trying to achieve with the hardware you select for the procurement project?
- Purpose
The first thing you need to do when starting on a project is ask "why"? What problem are you trying to solve? Once you explicitly define the problem, it becomes easier to evaluate possible solutions.
- Scope
A project's scope defines the outputs or deliverables of a project. What is the overall outcome of the project? How will the output of the project solve the problem? What features will the end result have?
- Objectives
The objectives are areas of focus of the project, and can be listed as discrete goals. Projects are usually constrained by an overall budget and time-frame. Objectives can break down the overall constraints of the project and apply them to individual aspects. Typically, good objectives follow the SMART principle, in that goals must be:
o Specific - well-defined and clear output
o Measurable - You know when the goal has been accomplished, or how much progress has been made
o Attainable - Goals are realistic and can be achieved within the project's constraints
o Relevant - The goals are worthwhile and make sense in the context of the project
o Time-bound - Goals should have a time limit
The executive summary should be well-articulated: clear, concise, and use correct spelling and grammar. The intended audience for the executive summary can be assumed to have basic technical knowledge, but are not networking experts. You should aim for 200 to 300 words.
PART 2 - Network specifications and diagram
Network Specifications
You have been given a rough sketch of the network topology below. You are to draw the network using Visio, subnet the network (see part 3), and assign port numbers and IP addresses to ports.
Network Structure
Hardware
- Only include one switch in you diagram for each LAN or WLAN (even if more are required)
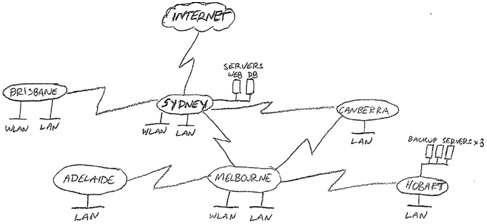
- The Internet router port address is 104.200.16.26/30
- The Sydney router is connected to the Internet, and provides access to the public backbone containing a web server and a database server.
PART 3 - Subnet the network using VLSM, and assign IP
addresses to the appropriate devices.
Each location has the following number of hosts
Sydney, Melbourne, and Brisbane each include a wireless LAN for clients to use.
|
Location
|
Workstations
|
WLAN addresses
|
|
Sydney
|
400
|
30
|
|
Melbourne
|
70
|
14
|
|
Brisbane
|
150
|
14
|
|
Canberra
|
50
|
|
|
Adelaide
|
80
|
|
|
Hobart
|
15
|
|
Subnetting
Use VLSM to subnet the network topology using a public class B network. You are to use the table format below to provide the subnet details.
Table 1. Subnets (including WAN subnets)
Spreadsheet Columns: Subnet name, subnet address, subnet mask (in slash format), first useable address, last useable address, broadcast address, static address range and DHCP address range (all addresses to be in dotted decimal notation)
Table 2. Router Interfaces
Spreadsheet Columns: Location, interface, IP address, subnet mask (in slash format)
Table 3. Servers
Spreadsheet Columns: Location, server name, IP address, subnet mask (in slash format)
Additional requirements:
- Choose one public B class network address for the entire network and subnet this block of addresses to optimise spare addresses for future expansion.
- Place the WAN subnets in the blocks directly following the LAN address space.
- Add 100% to each subnet to allow for growth in the number of hosts specified for each LAN (i.e. workstations × 2). Do not allow for any growth in the number of servers or size of WLANs
- DHCP will to be used for IP address allocation for hosts in each subnet and these ranges are to be allocated for each LAN.
- Static IP addresses are to be allocated where appropriate.
- The ISP has given us an IP address of 104.200.16.26/30 for our Internet connection at Sydney.
PART 4 - Research and source appropriate devices justifying choices (feasibility, efficiency, etc.)
You are to research and submit a project procurement plan for the Brisbane networks. The devices you must include are routers, switches, and wireless access points. Make sure the devices you select can handle the number of workstations required at the site, and provide a good quality of service to wired and wireless users.
Your project plan and final recommendations should be based on a Weighted Decision Matrix (similar to the WDM you did in the Procurement Practical). You are to compare five (5) devices from each category and to base the decision on reasonable and well-justified attributes.
The budget for all procurement is $10,000. You may exceed this if you can justify it well. Your project plan is to contain the following components:
Executive summary
- Briefly describe the goals of the procurement plan
Weighted Decision Matrix - hardware resource requirements analysis
- Include a written justification for priorities and attributes given in the matrix
- Create your WDMs in Excel and copy and paste them into your Word doc
Budget
- Create a well-presented table of the prices of all devices and the total cost
- Include hardware only, not labour
PART 5 - Cloud computing proposal
You have been asked to prepare a proposal about how cloud computing could be used to reduce the company's hardware, service, and energy costs. You are to consider the following three scenarios, and make a recommendation on which to choose:
1. Replacing ALL workstations within the organisation with thin clients, which will access a desktop environment provided by a cloud service provider (such as Amazon).
2. Replacing ALL workstations within the organisation with thin clients, which will access a desktop environment provided by a private cloud infrastructure, created in-house and based in Sydney.
3. Continuing to use workstations.
The company's current contract is $850 per workstation, per year, for hardware and service. On average, each workstation currently consumes 230 kWh per year of electricity. In making your recommendation, you should consider not just costs, but the security implications of moving to a cloud service.
Your proposal should not exceed 2000 words. You must provide citations for any references that you use.