Network Technology Assignment
Learning Outcomes tested in this assessment:
1. Critically Evaluate, design and implement both LAN & WAN systems,
2. Install and configure routers and switches,
3. Critically evaluate the performance of Link state in comparison to distance vector routing protocols,
4. Design Network management infrastructure.
Network Technology Assignment -
The assignment places you in the position of a computer network administrator required to setup a proposed network and configure the routers accordingly.
As administrator you will be required to make logical and justifiable decisions in order to produce feasible router configurations.
You are responsible for the configuration of all the shown routers.
The basic network requirements have been provided overleaf. An important consideration will be the method of implementation and verification.
You are required to think carefully and have a logical strategy in order that the configurations can be implemented with minimal error.
Your configurations must be commented with explanations. For example if VRF commands are issued then a comment must clearly explain what their purpose is.
The main topography has already been installed and is shown in Figure1.
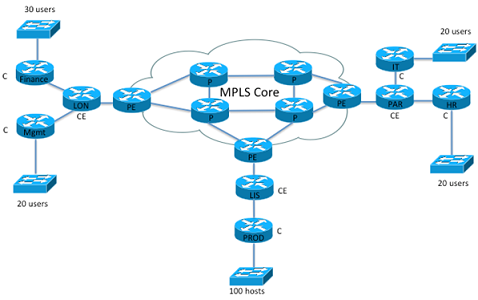
All routers shown in the diagram are Cisco 2800 Series routers.
Alternative designs are not required and will not be considered.
STANDARD MPLS VPN IS TO BE USED.
MPLS LITE OR ANY OTHER METHOD WILL NOT BE ACCEPTED
YOU ARE NOT REQUIRED TO CONFIGURE THE WORKSTATIONS
YOU ARE NOT REQUIRED TO IMPLEMENT A PHYSICAL NETWORK
The Assignment Brief -
As a network administrator, you are required to configure the CE routers and C routers of your company. The Telco company in each location has configured the P routers and PE routers in the MPLS Core cloud.
All of the network including the MPLS cloud are owned and administrated by the company. There are no external links to this section of the network. Other internal departments are already using the network but are not shown on the diagram Figure1.
CE routers provider facing interfaces have been assigned addresses as follows:
LON (Headquarter) 202.2.252.2/30
LIS 202.2.252.6/30
PAR 202.2.252.10/30
The following requirements have been agreed and must be implemented:
1. All LAN connections are to be directly connected using a FastEthernet link.
2. PAR HR is to reach LON Finance via an MPLS VPN
PAR IT is to reach LON Mgmt via an MPLS VPN.
PAR IT is to reach LIS Prod via an MPLS VPN.
3. LON Mgmt, LIS Prod, and PAR IT are to have a full mesh MPLS VPN connection.
4. PAR IT is to have a direct MPLS VPN link to LIS Prod. The link will additionally be protected by implementing IPSec.
PAR HR is to have a direct MPLS VPN link to LON Finance. The link will additionally be protected by implementing IPSec.
5. LIS Prod must not have any access to PAR HR.
LIS Prod must not have any access to LON Finance.
6. The Company has stipulated that all routers must be locally secure.
7. Each client router will distribute appropriate IP addresses to client workstations in an efficient manner using DHCP.
Assessment -
You are required to write a report on the commissioning of the network explaining the configuration, decisions taken and the strategy to confirm implementation.
Network decisions and justification
There are several aspects of the implementation which need to be decided. All decisions need to be explained and justified.
Router Configurations
This should not be a print out of a complete configuration. Only configurations made to implement the network need to be included. All configurations should be commented.
Present your configurations logically and coherently.
In other words the configuration details for a VPN should be given separately from other configuration details.
Strategy for Implementation and Testing
Implementation strategy should show a logical approach to the design and setup of the network.
Testing strategy should detail which tests, debugs etc should be used.
You may present the strategies independently or combined.
Report on how testing to be conducted with appropriate command such as debugs, ip route, ping test.
Discussion and Conclusion
Discussion can be at the end of the document or after individual implementations. If discussion is spread throughout the document then a brief summary should be given at the end.
Conclusion should summarise for the reader what has been achieved.
Attachment:- Assignment.rar