Information and Network Security Assignment
Q1. We consider the security services:
- confidentiality,
- integrity,
- authenticity, and
- non-repudiation
for a variety of simple protocols using symmetric or asymmetric cryptosystems, in a network environment where the two participants, Alice and Bob, are communicating in the presence of an adversary (attacker with malicious intent) Eve.
In the following scenarios for each of the four security services, describe whether or not it is achieved, and in either case give reasons.
(a) A → B : m||h(m)
(b) A → B : m||MAC(KAB, m)
(c) A → B : E(PUB, m)
(d) A → B : m||E(PRA, h(m))
(e) A → B : E(KAB, m||h(m))
Notation: m is the message, h() a cryptographically strong hash function, E() an encryption algorithm corresponding to the specified keys (symmetric for secret key, asymmetric for public/private key), MAC() is a message authentication code algorithm, KXY is a secret key shared between entities X and Y (symmetric algorithm), PUX is the public key and PRX the private key of entity X (asymmetric algorithm), || is concatenation function, X → Y specifies X sends to Y.
Q2. Alice and Bob agree to communicate privately via a protocol based on RC4, but they want to avoid using a new secret key for each transmission. Alice and Bob privately agree on a 128-bit key k. To encrypt a message m consisting of a string of bits, the following procedure is used:
(a) Choose a 16-bit seed (random value): r
(b) Generate the ciphertext c = RC4[h(r)||k] ⊕ m for the message, where h(r) is a cryptographically strong hash function that produces 128-bit message digest of the input
(c) Send the bit string h(r)||c
Answer the following:
(a) Suppose Alice uses this procedure to send a message to Bob. Describe how Bob can recover the message m?
(b) After how many messages should Alice and Bob change the secret key k to avoid RC4 key being repeated?
(c) Does increasing the bit size of the seed r make any difference in the previous part of the question? Explain why or why not.
Q3. Alice is using CFB mode of operation to encrypt a 16KB file to send it to Bob (1KB=1024 bytes).
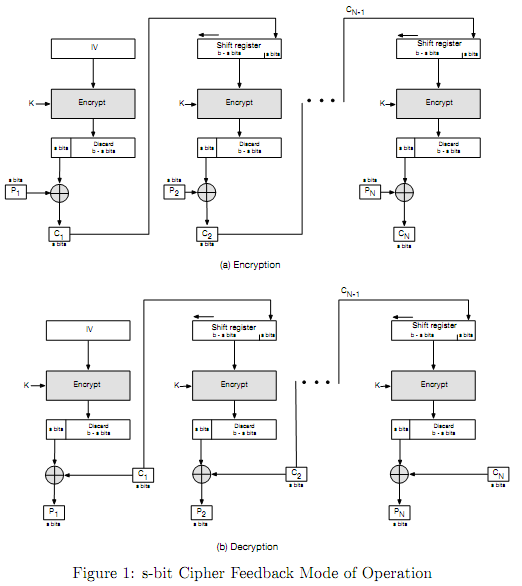
(a) How many ciphertext blocks will be produced if Alice uses 8-bit CFB-DES (DES or Data Encryption Standard algorithm as the block cipher in Figure 1)?
(b) How many ciphertext blocks will be produced if Alice uses 16-bit CFB-AES (AES or Advanced Encryption Standard algorithm as the block cipher in Figure 1)?
(c) If there is an error in transmitted ciphertext block C1, how many plaintext blocks will be corrupted when Bob decrypts the file for 8-bit CFB-DES?
(d) If there is an error in transmitted ciphertext block C1, how many corrupted plaintext blocks when 16-bit CFB-AES is used?
Q4. Joe is an overworked and under-appreciated programmer at "This Secure World" company. He is asked to write an RSA key generation algorithm that performs better than the competition. To increase the efficiency of his algorithm he decides instead of generating two random prime factors for the modulus part of every RSA key pair, to reuse one of the previous factors and only generate one new random prime number for the new pair. For instance if the algorithm is generating x RSA key pairs the value of n for these keys would be as:
n1 = p1 x q1
n2 = p2 x q1
n3 = p2 x q2
n4 = p3 x q2
. . .
etc.
This has increased the efficiency of his algorithm by reducing the time required to test the primality of the randomly generated numbers and for the first time in quite a while he is praised by his supervisor for the surprisingly good performing algorithm. The company is going to embed this algorithm in all of their hardware and software products. You are tasked with evaluation of the security of Joe's approach by either approving or rejecting Joe's idea. For either case you need to provide a compelling argument for or against the explained approach. You can use the following four values of n to argue your case (if needed).
n1 = 6707746877476258769687006155346667312135818167434246494098858837590302781071
n2 = 10154884310969769321427673109695437709100362015315810046444550032439143118393
n3 = 16589923032327209104008156227749326050568372812838589709379351079078499097041
n4=1575487835625540131816354221478432115692476442918739107617773841300854393383
Q5. Eve (the adversary to Alice and Bob) intercepts the following communication between Alice and Bob:
- Alice: Let's use Diffie-Hellman key exchange algorithm to share a secret key
- Bob: Ok, let the prime be p = 21764036621498105787560256376487687131351962980131606042071496200654587822341 and the primitive root (generator) g = 5
- Alice: Using your selected parameters my public key is YA = 7268937201146768929726789293736151850236699943837892054706367857897711254113
- Bob: My public key is YB = 276234186282125810839720184172914090708234028484467282900291170147002076321
- The rest of the communication is encrypted with KAB
(a) In the above scenario can Eve recover the shared secret key KAB using the captured messages? Explain what stops Eve from recovering the key or how she can calculate the value of the shared secret.
(b) Knowing the private key of Alice as XA = 278623657769 what is the value of KAB?