Answer the following problems.
problem 1) Count-to-infinity is the common problem with distance vector routing protocols. One partial solution is a heuristic known as split horizon with poison reverse.
(a) Draw simple network and give a circumstances in which that network changes and split horizon with poison reverse prevents count to infinity. (Note: This needs neither a complicated network nor a complicated scenario.)
(b) Draw simple network and give a circumstances in which that network changes and split horizon with poison reverse doesn’t prevent count to infinity. (Again, you can perform this with simple network and straightforward circumstances.)
problem 2) Consider iSLIP crossbar scheduling algorithm.
(a) For router with N ports, find the maximum number of iterations iSLIP could take to complete?
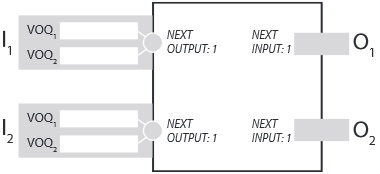
(b) Place packets in virtual output queues (VOQs) shown below such that during the next time slot the iSLIP algorithm takes 2 iterations to complete and each output is given a packet to transmit. Suppose that input 1 is the next input in both output 1's and output 2's round robin schedule.
c) Place packets in virtual output queues (VOQs) shown below such that during next time slot the iSLIP algorithm takes 1 iteration to complete and each output is given a packet to transmit. Suppose that input 1 is the next input in both output 1's and output 2's round robin schedule.