problem 1) A small company has network topology shown below. In this topology: Three Ethernet segments (L1, L2, L3) are interconnected with transparent bridge B and router R. Nodes E, F, I, and J are end systems. End systems don’t forward packets.
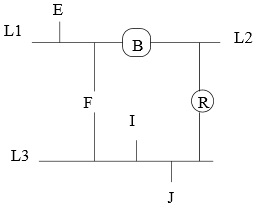
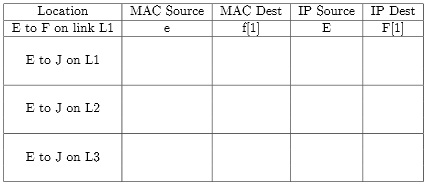
a) In this problem, use following notation: the MAC address of node E is e (lower case), its IP address is E (UPPER CASE). If node has multiple IP or MAC addresses, use index of segment to distinguish between them. Such as, host F has two different IP addresses, F[1] and F[3], as it is on two LANs. The first line in the table provides an ex entry for a packet from E to F on link L1.
Assume host E opens a connection to the Web server J. In the following table, give the MAC and IP source and destination addresses of the SYN packet of the TCP connection as it is observed travelling on links L1, L2, and L3 (i.e. fill in the next 3 lines).
b) The administrator has allocated class C addresses to each of the routed IP subnets. All the networking parameters of the different nodes in the system are statically configured. At some point, the company wants to move server J from link L3 to link L1.
(i) What changes are required to configuration of J?
(ii) What changes are required to configuration of R? (Don't worry about DNS for any of these problems).
(iii) What other nodes need to be updated?
c) At a later time endsystem E is moved to link L2. What nodes should have their configuration changed and how? Because of high network utilization in L3, the administrator reduces network load in L3 by segmenting it.
d) What type of device should be used if the administrator wishes to minimize his work? Give a reason for your answer.
e) What kind of device should be used if a significant portion of network traffic is broadcast (primarily ARP traffic) on the LAN? Give a reason for your answer.