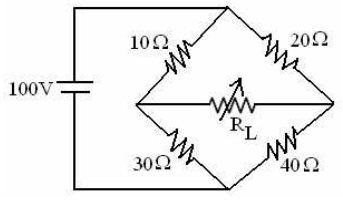
problem 1: Find out the load resistance to receive maximum power from the source, also find out the maximum power delivered to the load in the circuit as shown below.
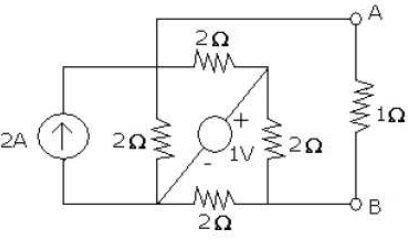
problem 2: Find out the current in the 1? resistor across A, B of the network shown in figure below using superposition theorem.
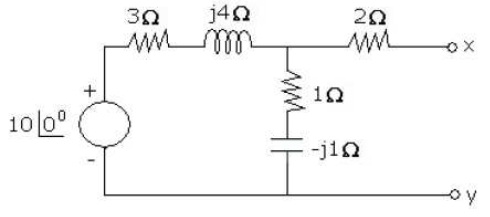
problem 3: Find the load impedance for maximum power transfer in the network of Figure. If the load is purely resistive, what will be its value for max. power transfer? Also, find the maximum power taken by the load in both cases.
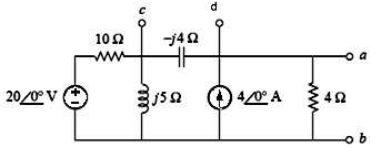
problem 4: Find the Thevenin’s equivalent circuit of the circuit shown in figure below as seen from:
a) Terminals a-b
b) Terminals c-d
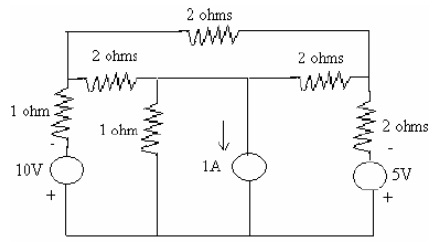
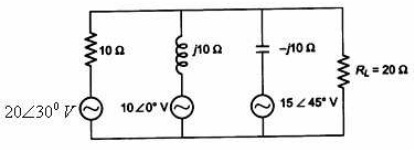
problem 5: Using Millman’s theorem find out the current via RL in the circuit as shown in figure below:
problem 6: For the below network draw the graph and prepare down the procedure to obtain cut set matrix.