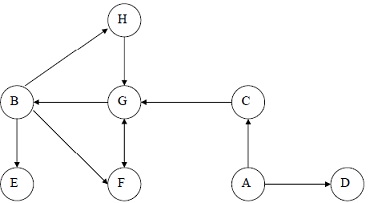
problem 1)a) Draw the depth first search tree and a breadth first search tree for the graph shown below, taking node A as the initial node stepwise.
b) What are circular queues? How do they differ from general queues? Describe how elements can be added and removed from the circular queue.
problem 2)a) prepare an appropriate function to delete any node from a doubly linked list. For the set of elements given below trace the function stepwise to delete nodes with values 12, 65 and 72 respectively with appropriate pictorial representations of the nodes and their links.
12, 14, 24, 33, 65, 42, 54, 72.
b) prepare the function to add two long integers represented in the form of two singly linked lists. (Note: Each digit of the number is a node of the linked list) The function should return a pointer to the resultant list.
problem 3)a) prepare a function to create a tree for a postfix expression. Trace the same stepwise for the expression (A+ ((B-C)*D) ^E^F) by first giving the equivalent postfix expression.
b) prepare a note on hash functions.