problem 1: The schematic of the traffic light controller is as shown in figure below. There are three control buttons on the panel: HAZ (Hazard), LT (Left) and RT (Right). Whenever, HAZ is clicked, the entire six lights blink in unison pointing out the situation. Though, whenever LT is clicked, only the left three lights (L1, L2 and L3) blink pointing out the left turn and likewise, whenever RT is clicked, only the right three lights (R1, R2 & R3) blink pointing out the right turn.
Please prepare the VHDL code fulfilling such specifications. In order to integrate the clicking and display functionality, it is essential to interface the traffic light code with proper mouse and monitor interfacing codes. There is at least the given number of modules in the correct working of this system:
A) Traffic light controller module.
B) Mouse interfacing module.
C) Monitor interfacing module.
D) Video PLL (a specific code for viewing on the monitor screen).
E) Main module interconnecting the sub-modules via port-mapping.
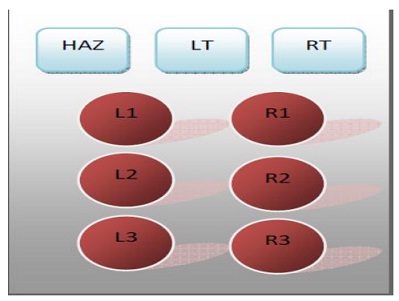
Figure: Traffic Light Controller Schematic.
The output:
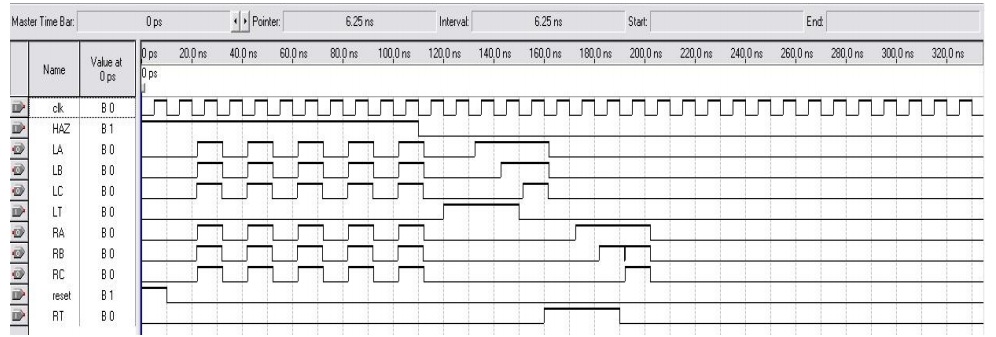
Lab reports should follow the template illustrated below:
A) Front page with the title of the project, date and name of the students all along with their IDs.
B) Introduction on the working of the system all along with a targeted issue which is addressed.
C) Design methodology describing the hierarchy of the system along with the different modules, their role and respective ports.
D) Results with a detailed description of the behavior of the system.
E) Conclusion.
F) Problems faced (if any throughout the coding and implementation stages).
G) Screenshots for simulated waveforms, pin assignments, RTL view and state machine view. (RTL and state machine viewers can be found under Tools –> Netlist Viewers)
H) Contributions including the names of the individual team members and the name of the modules coded by them.
It must be a hierarchical code having two modules: traffic light module and clock division module. Moreover, you require to port map these two modules in a main program.