Software Development Tools Assignments
You are required to complete three (3) assignments.
Assignment 1 -
Question 1: Create a subdirectory in your home directory and then in the subdirectory create a file welcome.txt having a short message in it. Try to:
- set the directory's permission bits so that the owner has executable access.
- make the subdirectory the current directory;
- list the subdirectory;
- display the contents of welcome.txt;
- create a copy of welcome.txt in the subdirectory.
Repeat the experiment, but the owner has read access.
Give all of the command lines of performing above activities. Finally, answer the following questions.
- If a directory has "read" permission bit, what operations can you perform on the directory and/or the files in it?
- If a directory has "executable" permission bit, what operations can you perform on the directory and/or the files in it?
Question 2: Use examples to describe the differences in the substrings matched by the patterns which are specified by the following regular expressions.
- ab.cd and ab*cd
- ab.*cd and abb*cd
- ^abc and ^abc$
- [abc]d and [^abc]d
- [A-Z][_a-zA-Z0-9]* and [A-Z_][a-zA-Z0-9]*
(Note the regular expression "x*$" could be described as a line has "zero or more x at the end of the line". An example for "x*$" can be 'a jumping fox')
Question 3: Read find online manual page, then
- Give the command line of searching for all SUID and SGID programs in /usr/bin
- Give the command line of listing all the subdirectories in the current directory
- Give the command line of producing a long listing of all files in /usr/bin whose size are more than 750Kb.
Question 4: List the command line of performing the following activities
- Use tar to create an archive (don't use the z or j option) of all the files in the current directory.
- Compress the tar file with gzip.
- View the contents of archive with gunzip and tar
- View the contents of archive without using gunzip but use the tar instead. (Hint: find the right option from the man page).
- Create a subdirectory of the current directory.
- Use tar to unpack the archive into that subdirectory.
Question 5: Assume you have a simple text file called myfile. Describe what the following sed-command lines do on myfile.
1. sed "s/the/a/g" myfile
2. sed -n "s/[A-Z]/&/gp" myfile
3. sed "32,45 s/[()]//g" myfile
4. sed "/^$/d" file
5. sed "s/\([0-9]\)-\([0-9]\)/\1\2/g" myfile
Here is a sample question, what does sed 's/fox/ox/g' myfile do to the myfile?
Assignment 2 -
Question 1: Create a LATEX document, which should be in 11point font
- Add a title with your name and the date(for instance Feb 14, 2017)
- Add a table of contents
- Add a section introducing yourself and all the courses you enrolled.
- Include a piece of verbatim text - this might be a program (either Bash script or C code fragment).
- Add the following unnumbered formulae x = -b±√(b2-4ac)/2a and
- Typeset the following numbered mathematical formula (1).
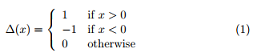
- Create a floating table with the caption. It should look just like the one in Table 1, except that the table number will be different(Don't have to use the multirow package).
- Include a short biography of you, along with your recent photo.
|
Category
|
Tool
|
|
Command
|
Description
|
|
Editor
|
emacs
vi
|
Emacs extensible text editor
Visual editor
|
|
Scripting
|
bash
per1
|
GNU Bourne-Again Shell
Practical Extraction and Report Language
|
|
Document Managment
|
rcs
LATEX
make
|
Revision Control System
Document Typesetting Package
Managing Project Utility
|
Table 1 - Some Unix Utilities
Question 2: Write a well structured Bash script to delete comments from a C program. In Bash script, you may use sed commands or other Linux utilities. The standard comment or commentline in C programs starts with the two-characters token (/*) and ends with the two-character token (*/). Assume that each comment line contains the start and end tokens without any other statements before and after. You need to pay attention to the following cases:
/* a comment line in a C program */
printf("It is /* NOT a comment line */\n");
x = 5; /* This is an assignment, not a comment line */
[TAB][SPACE] /* another empty comment line here */
/* another weird line, but not a comment line */ y = 0;
You can test your Bash script on a C program containing all above four lines. The expected output should look like
printf("It is /* NOT a comment line */\n");
x = 5; /* This is an assignment, not a comment line */
/* another weird line, but not a comment line */ y = 0;
where TAB and SPACE stands for the Tab key strokes or white spaces.
Question 3: Write a short but well structured Bash script that, given the name of a file as an argument, reads the file name and creates a new file containing only those lines which have one word in it. Here is an example of the input file. This is a special text file
There
are 20 students in the class.
[TAB][SPACE] Nearly
half of them are enrolled in FoS. The rest are in Faculty-Of-ES.
The output file from the script should look like
There
[TAB][SPACE] Nearly
Faculty-Of-ES.
Well structured means the script should have the error and robustness checking.
Assignment 3 -
Question 1: Write a makefile that reflects the dependency relationship between a set of C program source files which comprise an application as shown in Figure 1.
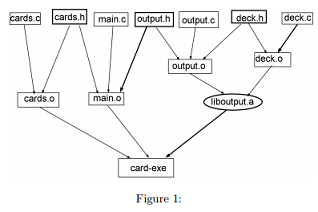
The arrows point to the dependent file from the file on which it depends. In other words,
1. The application card-exe is created by linking together the object modules main.o and cards.o and the object library liboutput.a.
2. The object library is built from the object file output.o and deck.o; these object files depend upon their corresponding source files.
3. output.o additionally depends on deck.h
4. The header file cards.h contains calling definition (prototypes) for the functions in cards.o and deck.h containing prototypes for deck.c
5. all files which call functions defined in deck.c will need to include deck.h.
6. main.c calls functions from cards.c and output.c, cards.h and output.h must be included in main.c
Question 2: Use a small text file to experiment with the RCS system. Note that RCS treats all ASCII file the same way; the files do not necessarily be programs, though usually are programs. Specially you should
- Place a $Log$ keyword in the file
- Complete a set of check in operations which result in the RCS file structure depicted in Figure 2.
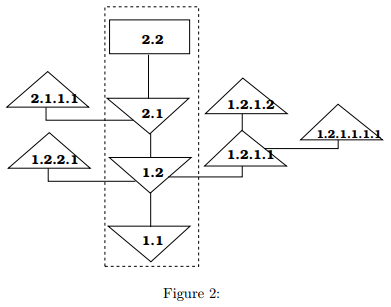
You will need to make small changes to the source file between check-in operations.
- Associate a symbolic name with revision 2.1.1.1
- Make the branch containing revision 2.1.1.1 the default branch
- Use rlog to verify the RCS structure.
Give all of the commands or command lines used to perform each of above activities, along with a brief description.
Resource Materials -
Text book:
There are a number of excellent texts about the Unix operating system. Some are brief introductions, while others are much wider in scope. Some texts also include some programming guidance. We have chosen the A Practical Guide to Linux Commands, Editors, and Shell Programming by Sobell. This is an excellent book. It is perhaps less tutorial in style than some other books, but it contains a wealth of detailed, well organized information. While it is not the appropriate choice for someone wanting a quick introduction to Unix, it is ideal as a long term companion.
You may choose to use or consult other Unix texts rather than the recommended text. This is acceptable and as long as you are able to complete the exercises and can cover the conceptual material contained in chapters 2, 3 and 4.
Readings:
These are supporting documentation not covered by the textbook. Also included for your convenience are copies of some Unix man pages. The largest part of the Readings is the complete GNU Make manual, which you should find useful in many other courses.
Course DVD-ROM:
The course DVD-ROM contains a complete pre-installed Virtual Debian system created from the Department's Debian/GNU Linux Distribution.
This DVD-ROM is for emergency use only. It is for students having trouble installing Debian Linux on their computer-they will have access to a Linux distribution that will allow them to do the exercises and assignments without falling behind-while they sort out the problems of their installation.
A virtual operating system is no substitute for an installed operating system- remember this is not the only course you will do that will require access to a Linux operating system-it is far better to install the Operating System rather than rely on a virtual system.
WWW
All course material is available from the Course Home Page accessible via the USQStudyDesk
The course webpage described above is your primary point of contact with the university for this course. You can submit assignments via this site, and also retrieve results and feedback.