1. Prove asymptotic bounds for following recursion relations. Tighter bounds will get more marks. You may use the Master Theorem if it applies.
1. C (n) = 3C (n/2) + n
2. G (n) = G(n - 1) + 1/n
3. I (n) = I(n/2) + n/ lg(n)
2. Describe a (p,q)-tree as a rooted tree where every internal node has between p and q (inclusive)children. Use the Master Theorem to give asymptotic bounds for height of the tree. You can suppose both p and q are constants with 2 ≤ p ≤ q.
3. Dominos
A 2 × 10 rectangle filled with ten dominos, and a 2 × 2 × 10 box filled with ten slabs.
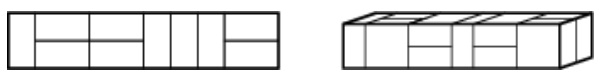
1. A domino is a 2×1 or 1×2 rectangle. How many dissimilar ways are there to completely fill a 2× n rectangle with n dominos?
2. A slab is a three-dimensional box with dimensions 1 × 2 × 2, 2 × 1 × 2, or 2 × 2 × 1. How many dissimilar ways are there to fill a 2 × 2 × n box with n slabs? Set up a recurrence relation and provide reasonable exponential upper and lower bounds.