problem 1)
(a) Assume that search tree has root A, which has children B, C, and D, that B has children E and F, that C has children G, H, I, and J, and that D has child K. Also, assume that nodes F and I are goal nodes.
i) Draw the search tree.
ii) What is the branching factor of node C?
iii) List the order in which the nodes are visited:
1) Breadth First Search
2) Depth First Search
3) Iterative Depth First Search
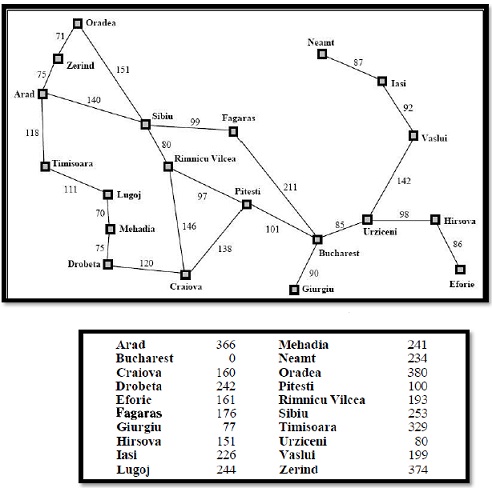
(b) Given the map of Romania in the given below and a list of admissible heuristic in the table below, apply the A* search algorithm to determine the path from Oradea to Bucharest.
problem 2)
(a) Differentiate between propositional logic and first-order logic.
(b) Use truth tables to verify the following equivalence:
(P v Q) v R ≡ P v (Q v R)
(c) Represent each of the following sentences in the first order logic
i. Aliens are red or green.
ii. At least one alien has spots.
(d) Given that the volume of a cylinder is given by . prepare a Prolog predicate which find outs the volume of the cylinder. The user should be able to input the value of the radius and height. The program must display the volume.
Sample run
Enter Radius: 4.
Enter Height: 5.
Volume of Cylinder: 251.32741228718345