Q1. By using 256 gray level shades to symbolize an image, draw two histogram shapes, one to symbolize an image that appears very dark and the other to symbolize a bright image.
Q2. How many bits would be needed to store an image of size 240 × 320 and 64 levels of the gray shades? Determine the number of bits required to store the colored image with similar number of levels for each color component?
Q3. Here is the image segment:
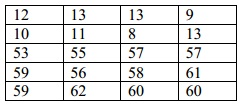
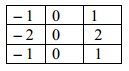
Convolve it with the given mask and point out the output for the pixels with intensity values 55 and 56.
Q4. Is it possible for two various images to encompass the same histogram? Validate your answer.
Q5. How do you detect the lines in an image? Point out appropriate masks for detecting the lines.
Q6. Name four statistical properties which are used on the gray level co-occurrence matrices to quantify texture of the image segment.
Q7. describe how is the chain code employed for the image description?