Answer the following problems.
problem 1)
a) A useful analogy can be made between knowledge engineering and programming. Both activities can be seen as consisting of four steps. What are they?
b) Taking a grocery shopping domain as an ex, describe how you would break it down into smaller clusters of knowledge, work on each cluster separately and then examine how they fit together. One good way of decomposing the domain into clusters is to consider the tasks facing the agent. Give the name you would choose after dividing the domain into five clusters.
problem 2)
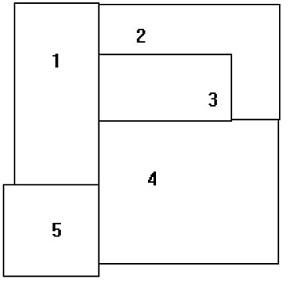
a) A famous problem in mathematics concerns colouring adjacent planar regions. Like cartographic maps, it is required that, whatever colours are actually used, no two adjacent regions may not have the same colour. Two regions are considered adjacent provided they share some boundary line segment. Consider the following map below.
i) Draw a graph to show how would you represent the said regions.
ii) prepare down a Prolog representation to represent your above information by unit clauses, or facts.
iii) How would you declare colourings for the regions in Prolog also using unit clauses.
iv) prepare Prolog definition of Conflictive colouring, meaning that two adjacent regions have the same colour.
v) prepare another version of “conflict? that has more logical parameters.