Project Description:
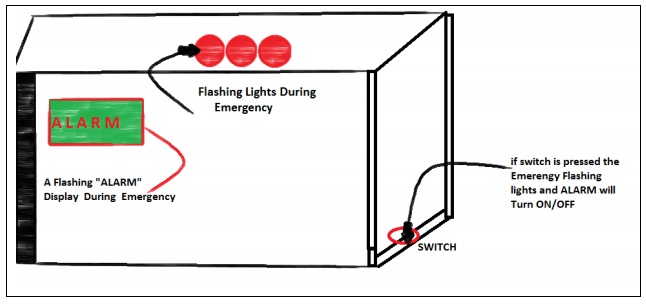
In this Project you will simulate a Security Alarm system using the Quick flash board. A switch is placed as shown in the figure below. The main goal of this project is:
Task 1: If anyone entering to the house steps (Presses) the switch the three Flashing Lights must turn ON/OFF and a flashing (ON/OFF) “ALARM” must be displayed on the Green Screen shown.
Task 2: For every presses of the switch make the flashing for only 5 times.
Further Work if Interested:
Improve the previous project by adding another input device (RPG): to make the alarm stay till the user handles the situation and rotates the RPG to 11 positions.
Hint:
A) You can use the push button switch given in the board as SW3 as the triggering input
B) D4.D5 and D6 diodes as the flashing Lights and use the LCD to display “ALARM” (ON/OFF).