Q1. In brief describe the dynamic programming method by using Floyd’s algorithm for the problem of all-pairs shortest path as an illustration.
Q2. Describe the concept of greedy method. Consider the Knapsack instance,
No. of objects (n) = 3
Capacity of Knapsack (M) = 20
Profits[ P1, P2, P3] = [25,24,15]
Weights[w1,w2,w3] = [18,15,10]
Determine the optimal solution.
Q3. prepare down an algorithm to create a heap from the elements of a given array by using the bottom up approach. Illustrate the time complexity?
Q4. What do you mean by AVL tree? Describe the need for rotation of AVL trees. Create an AVL tree for the list 8, 9, 11, 6, 5, 7, 10 by using the successive insertion. Describe the steps clearly.
Q5. Describe the concept of 2-3 tree. describe how can keys are inserted to it. Comment on the efficiency of search operations on a 2-3 tree.
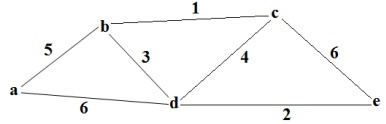
Q6. What do you mean by Spanning Tree and Minimum Spanning Tree (MST)? prepare down the Kruskal’s algorithm to determine MST and apply the algorithm on the given graph: