Q1. Describe the Haar transform which is used for wavelet coding.
Q2. Define the term transformation which is used for the scaling and rotating an image regarding the origin.
Q3. A gray scale image having a single object has been transformed into a binary image. Point out how ‘thinning’ operation can be taken out on the object.
Q4. Deduce the Laplacian of Gaussian (LoG) filter. Describe the purpose which it serves?
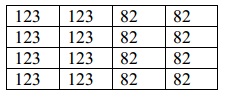
Q5. Describe the LZW coding scheme by utilizing the given image segment:
Q6. Illustrate how the ‘hit or miss transformation’ operation is taken out by taking an illustration. Illustrate the use of this morphological operation?