Q1. How would you identify a loop in a linked list? prepare down a C program to detect the loop in a linked list.
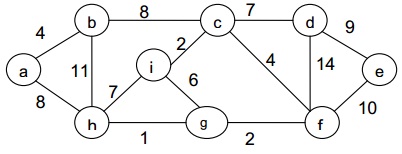
Q2. What do you mean by minimum spanning tree? Work out the Prims algorithm to determine the minimum spanning tree of the given graph:
Q3. Illustrate the meaning of Huffman trees? prepare down the algorithm for the same. Draw Huffman tree for the set of weights {1, 2, 3, 3, 4}
Q4. prepare down an algorithm to determine the successor of an element(x) in the binary search tree.
Q5. For the given sequence find out the binary heap obtained if the keys are inserted one by one in the order given to an initially empty heap:
16, 14, 10, 8, 7, 9, 3, 2, 4, 1
Q6. Illustrate the difference between the Merge Sort and Quick sort?
Q7. Illustrate the difference between the binary-search tree property and the heap property? Can the heap property be employed to print out the keys of the n-node tree in sorted order in O(n) time? Describe why or why not.
Q8. prepare detail note on any three of the given:
a) Circular queue and priority queue
b) K-way merge sort
c) Linear and quadratic probing
d) Game tree