problem 1: Suppose there are 64 different op codes and 19-bit instruction word in a computer system. Two bits in the instruction are reserved to point out the addressing mode.
a) Draw a box style sketch of a CPU showing and labeling Special Purpose Registers:
PC, IR, MAR and MDR and General Purpose Registers: Accumulator, R0-R3.
b) How many different memory locations can this system access by using direct and absolute addressing mode?
c) How many different memory locations can this CPU access by using base or offset addressing mode, if a 14-bit general purpose register serves as the base and can be loaded with any value?
problem 2: Consider an 8-bit system with 32-memory locations (numbered from 0 to 31) and 8 different instructions. Suppose that op code for "Load Accumulator" instruction is 510 and for "Add" instruction is 210. At this moment, the program counter register PC includes the value 00100 and is about to increment, memory locations contain the given values:
Address Contents:
01101 00110110
01100 01110100
01011 10111000
:
00110 01001100
00101 10101011
00100 01111000
Perform two fetch-execute cycles, present each step of the cycles and the contents of each special-purpose register at the starting and at the end of each step of the cycles in binary.
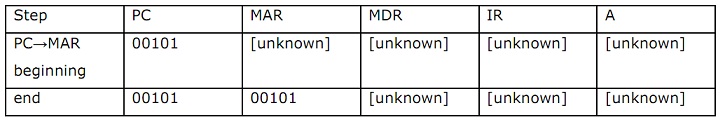
If you believe there is no information on the contents of a particular register, point out it as [unknown] (ex: MDR [unknown]). If overflow takes place, the MSB is stored in a single-bit flag register and not counted in Accumulator. Express the final contents of Accumulator in both binary and decimal. For your answer, use the given table (two first lines are given as sample):
problem 3: Draw a memory map for a system with a memory capacity of 512MB. Each memory location in the system is 8 bits. Suppose that the system consists of one 4MB memory block used as ROM residing at the bottom of the memory followed by one 16MB module and one 8MB module of RAM. The rest is conventional memory, except for 1MB block at the top used as cache memory. Point out the position of each memory module in your memory map. In hexadecimals, label the starting byte address and ending byte address of each memory block (including empty space). And also, label the size of each memory block in MB.
problem 4: An interrupt is produced by a laser printer as a means of allocating the CPU time. Describe the sequence of events in this computer system by using polled type of interrupt handling.
problem 5: A multiplattered HDD is divided into 40 sectors and four hundred cylinders. There are four platter surfaces. The total capacity of the disc is 256MB. A cluster comprises of four blocks. The disc is rotating at a rate of 3600 rpm. The disc has an average seek time of 24 msec.
a) Determine the capacity of a cluster for this disc?
b) Determine the disc transfer rate in bytes per second?
c) Determine the average latency time and the average access time for this disc?