1 Part I
1.1
How could you carry out a floating point comparison? You must include two exs, one in C-shell and one in Bourne shell.
1.2
Describe the getopts command and prepare the sample shell script which uses getopts.
2 Part II :Bourne Shell
You must prepare the following problems in Bourne shell and design appropriate functions for each of them.
2.1
prepare the alarm clock script which sleeps for a number of seconds and then beeps and displays a message after that times has elapsed. The number of seconds is set based on an input argument.
2.2
Use a recursive function to print each argument passed to the function, regardless of how many arguments are passed. You are allowed to echo only first positional argument (echo $1).
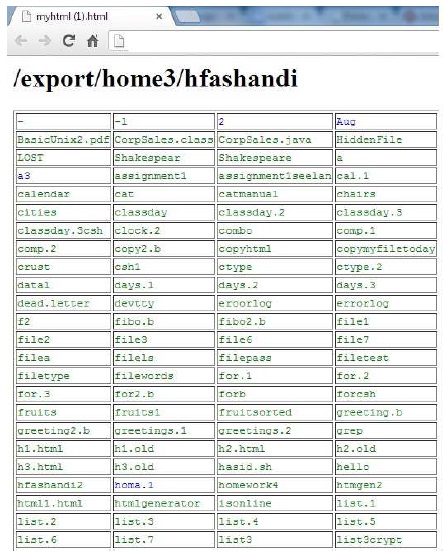
2.3
prepare the Bourne shell script which create the HTML file. This file must have a table of 4 columns and n rows. The table’s elements are the contents of a directory. Directory names are written in blue and ordinary file names are written in green.
mars% ˜/htmgen2 > myhtml.html
The above command line creates an html file myhtml.html and this file is shown in above figure.
2.4
prepare the Bourne shell program which displays the following menu to the user:
Would you like to:
1. Look someone up
2. Add someone to the phone book
3. Remove someone form the phone book
4. Quit
Please choose one of the above (1-4):
For option 3, if multiple entries are found, then program would prompt the user for the entry to be removed:
More than one match, please choose the one to remove:
AAA Brown Remove[y or n]: y
AAA Blue Remove[y or no]: n
Part 3 Bourne shell and C-Shell
You must prepare two scripts for each of the following problems: one in Bourne shell and one in C-Shell.
3.1
prepare a program called isyes which returns an exit status of 0 if its argument is ”yes” and 1 otherwise. For purpose of this exercise, consider y,yes, Yes, YES and Y to be valid ”yes” arguments.
3.2
prepare a program called counttime which prints number of hours and minutes that a user has been logged on to the system (suppose that this is less than 24 hours). The name of the user is an input argument.
3.3
prepare a Shell script that checks the validity of a userid that is passed as an input argument. If the userid is available on mars it would display the suitable message.
3.4
prepare the shell script which looks at the name on on the command line and responds with the output string Web page if the name ends with html or with htm and with the output string applet if the name ends with class
3.5
prepare a shell script which changes permissions of all the files in the present directories which ends with scpt so that they are executable by everyone.