problem 1: Find the minimum weighted path length P for six weights 4, 15, 25, 5, 8, 16. Draw the huffman tree also for the given weights. Find the huffman code for each weight.
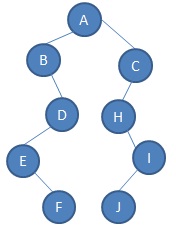
problem 2: Find the Inorder, preorder and postorder traversal for the given tree:
problem 3: Convert the following expressions in binary expression tree.
A - (B*C) + D $ (E*F)
(b) (A-B) * (B-C)/(C-D)
(c) (3x+4y) - (5x/7y)2
After constructing the expression tree find the inorder, preorder and postorder traversals.
problem 4:
(a) Create a binary tree. Given,
Post Order: D H I E A J F N P G C B.
Inorder: D H A I E B F J C N G P
(b) Create a binary tree. Given,
Preorder: D B C A G E F H I J.
Inorder: B C D G E A H F I J
(c) Create a binary tree. Given,
Preorder: K A E F C D H L B
Inorder: E A C F K H D B L
problem 5: Perform the following operations in BST:
Insert Z, A, C, D, B, E, F, N, M, P, T, U, R, O, Q.
Delete M and then D.
problem 6: Construct an AVL tree by inserting the following elements in order of their occurrences: 44, 10, 11, 96, 7, 14, 53, 47, 50, 101, 4, 1
Then Delete 7, Delete 47 and then delete 101.
problem 7: A 3 way search tree constructed out of an empty search tree with following keys in order as given: D, K, P, V, A, G. Then Delete A and K.