Executive Proposal Project
The purpose of this project is to evaluate the student's ability to research and evaluate security testing software and present a proposal for review by executive team members. By completing the document the student will also gain practical knowledge of the security evaluation documentation and proposal writing process. The project will enable the student to identify and understand the required standards in practice, as well as the details that should be covered within a proposal.
Project Deliverable
- Using the Case Study presented in this document, to complete an executive proposal.
- Provide a threeto five page proposal summarizing purpose and benefit of chosen security software to the executive management team.
- The student will evaluate and test security testing software for purposes of testing corporate network security. The purpose of the software is to measure the security posture of the organization by identifying vulnerabilities and help prevent future attacks and deter any real-time unknown threats.
- The proposal should effectively describe the software in a manner that will allow the executiveteam members to understand the purpose and benefits of the software to approve purchase.
Guidelines
- Evaluate and select a security tool for recommendation that you learned about in theiLabs modules or the EC-Council text books.
- The proposal document must be 3 to 5 pages long, conforming to APA standards. See "Writing Resources" in the online classroom where you'll find help on writing for research projects.
- At least threeauthoritative, outside references are required (anonymous authors or web pages are not acceptable). These should be listed on the last page titled "References."
- Appropriate citations are required. See the syllabus regarding plagiarism policies.
- This will be graded on quality of research topic, quality of paper information, use of citations, grammar and sentence structure, and creativity.
- The paper is due during Week 7 of this course.
Project Description
The purpose of project is to write an executive proposal for a fictitious company called Medical Solutions Systems. The goal of the proposal is to persuade the executive management team to approve purchase of security testing software that can benefit the company's corporate network security by testing and identifying vulnerabilities before they are exploited by hackers. The proposal must include a detailed description of the software, its purpose and benefits.
Suggested Approach
- Research a security testing software tool that you practiced using in the EC-Council iLabs or from the textbook.
- Determine whether the tool would be beneficial in testing the security of a corporate network.
- Use the vendor's website to collect necessary information about the tool to be able to explain its purpose and benefit.
- Include 3rd party endorsements and case studies about the tool.
- Integrate the information from your own experience with the tool into your proposal. This may include results from the iLab exercises or your own test lab.
Company Description
Medical Solutions Systems
Medical Solutions Systemsis a startup medical research and development company. After five years of extraordinary success in the development of innovative medical and pharmaceutical products, Medical Solutions Systemsis on its way to becoming a major player in the medical research and development industry. However, due to its success, Medical Solutions Systemshas also become a major target of cybercriminals. Medical Solutions Systemshas been the victim of cybercriminal attempts to steal intellectual property and sell it to Medical Solutions Systems' competitors. It is suspected that the corporate network has been infiltrated from unauthorized sources more than once. In 2013, Medical Solutions Systemswas falsely accused of unethical research and development practices. The false allegations resulted in the defacement of Medical Solutions Systems' public website and several Denial of Service attacks at different times over a 9 month period that brought the corporate network to its knees. These attacks had a major impact on Medical Solutions Systems' ability to conduct business and resulted in undesirable publicity for the company.
Regardless of its security problems,Medical Solutions Systemshas continued to grow as a company. Its research and development departments have grown over the years, due to the expansion of the company, in proportion to the increase in its business making up over 40% of the human resources. Medical Solutions Systems' innovative research and development information is paramount to its continued success as a company. Although, no known attacks have occurred in last 18 months, the security of its network and intellectual property is still a major concern for the company. Because Medical Solutions Systemsis a still fairly young company, management has been hesitant to budget for expensive security projects. However, this point of view is beginning to change. Particularly, because one of Medical Solutions Systems'competitors, a major player in the medical research and development industry for over 40 years, experienced a loss of hundreds of millions of dollars in research data that was stolen from its corporate network by cyberthieves.
Background and your role
You are the IT Manager hired in 2015 to manage the physical and operational security of Medical Solutions Systems'corporate information system.You understand information security issues better than anyone else in the company. You also know that the network is vulnerable to outside threats because it has experienced attacks in the past and because you haven't had the resources to properly test the corporate information system to identify the vulnerabilities that might exist and take action prevent possible attacks. You have a responsibility to bring these concerns to the attention of the executive team and ask for approval to purchase the necessary testing software.
Your education and training have introduced you to variety of security tools for testing computer and network security. The majority of these tools you either only read about or have practiced using in lab environment. You have decided to research some of these tools and test them out in your own lab environment and choose one for recommendation to executive team.
You will need to present information that proves the chosen tool will be beneficial to the security of corporate information system. To accomplish this you will need to research the product, if possible, test the product in a virtual lab environment. If the tool is part of your iLab exercise, it is recommended that you practice using and testing the tool beyond the scope of the lab exercise. Based on your research and analysis, you will include this information in your proposal in way that the executive staff can understand and allowing them to make an informed decision to approve purchase of the product.
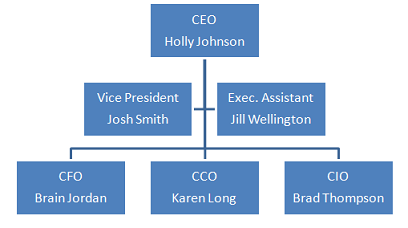
The executive management team of Medical Solutions Systems:
The proposal should include:
- Detailed description of the software and benefits.
- Include reviews, case studies and customer recommendations
- Include your own hands-on experience with the tool and test results
- Cost of product. Include additional costs such as training or hardware software that might be needed in order to properly deploy manage and maintain the software.
- How will the software impact the production environment? For example, the software may test for Denial of Service attacks. You need to explain any interruptions the test may have on business operations. You need to justify the need for such a test. Also explain how to you plan to minimize or prevent possible production outages.
The software should test for one or more of the following types of attacks:
- Denial of Service (DoS)
- Cross Site Scripting (XSS)
- Authentication Bypass
- Directory Traversal
- Session Management
- SQL injection
- Database Attacks
- Password Attacks
- Firewall/Router Attacks
- Operating System Attacks
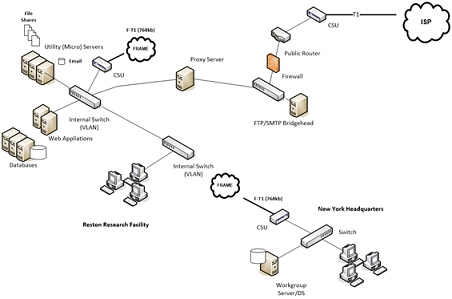
Corporate Office Network Topology
The Medical Solutions Systemsmain research and development facility is located in Reston Virginia. You have concerns about the sensitive information that is stored at this location as well as data that transmitted over the WAN to Medical Solutions Systems'New York City headquarters location, business partners and clients. The Reston facility is also where the Medical Solutions Systemsdata center is located. The data center is where Medical Solutions Systems'public website, email, databases and corporate intranet are hosted. The environment contains a mix of Microsoft and *NIX technologies.
- 45 Windows 2012 Servers
- 13 Windows 2008 Servers
- 15 UNIX Servers
- 2200 Windows 8 Desktops
- Web Servers: Apache and IIS
- Services: FTP, SMTP, DNS, DHCP, VPN
- Database: SQL, Oracle and MySQL
- Network: Cisco Routers and Firewalls