problem 1)a) Describe the concept of virtual machines. prepare a program in C to create a new process that lists the users currently logged on to the system and parent waits till the child process terminates.
b) With the help of diagrams, describe the current activities of a process when it executes and PCB of that process.
problem 2)a) Distinguish between a Process and a Thread. Describe the following threading issues to be considered in multithreaded programs:
i) fork() and exec() system calls
ii) Thread cancellation
iii) Thread pools
b) With essential diagram describe multilevel queue scheduling. For the following set of processes with the length of CPU burst time and arrival time in milliseconds is given:
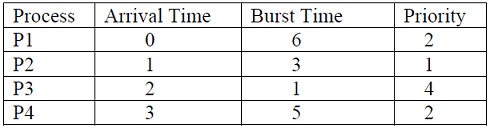
Draw the Gantt chart and find out average waiting time, average turnaround time for Preemptive Priority scheduling algorithm.
problem 3)a) Clearly show that with the general definition of semaphores with busy waiting, the value is never negative but with spinlock may have negative semaphore values.
b) What are two methods incurred to eliminate deadlocks in a system using process termination method. Consider a system with P0 through P4 and three resource types A, B, C. Assume resource type A has 10 instances, resource type B has 5 instances and resource type C has 7 instances. Following is the Maximum and Allocation matrices to the processes:
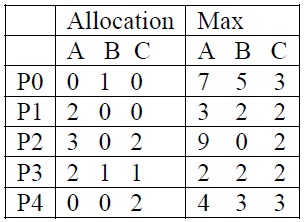
i) Check whether the system remains in safe state or not at time t=t0. Give the safe sequence.
ii) At time t1>t0, Process P4 requests additional resources ( 3 3 0). Check whether this request could be granted and safety of the system.