Q1. Let a and b signify the positive integers. Assume that a function Q is defined recursively as shown below:
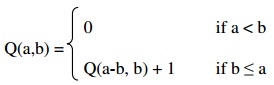
Determine the value of Q(14,3). describe what does this function do?
Q2. Consider the given arithmetic expression P, written in the post-fix notation:
P: 12, 7, 3, -, /, 2, 1, 5, +, *, +
Translate P, to its equivalent infix expression.
Q3. Determine the worst-case efficiency, best-case efficiency and the average-case efficiency of sequential search algorithm. Describe them by using asymptotic notations.
Q4. prepare brief notes on the Buddy Systems.
Q5. Illustrate in brief, the Divide-and-Conquer method.
Q6. Define the term priority Queues. Describe how priority queues can be implemented.
Q7. prepare down a C function which will delete kth element from the linear array of size n.