1. Construct a truth table for the following Boolean expressions:
a) ABC + A’B’C’
b) ABC + AB’C’ + A’B’C’
c) A(BC’ + B’C)
2. Simplify the following expressions:
a) A•B’ + B’•A + C•D•E + C’•D•E + E•C’•D
b) A•B + A•C + B•A
3. Apply DeMorgan’s theorem to the following expressions:
a) F = (V + A + L)‾
b) F = A’ + B’ + C’ + D’
4. How many input and output lines does a multiplexer contain if it has four select lines? Justify your answer.
5. How many output lines does a decoder contain if it has 10 input lines? Justify your answer.
6. Design a 4-to-1 multiplexer using AND, OR, and NOT gates. HINT: construct a truth table for this multiplexer using a maximum of a 2-bit combinations.
7. Convert 0010 11012 to hexadecimal.
8. What ASCII character is 0110 11012?
9. Two’s complement is a method of representing positive and negative integers in binary. Provide the 8-bit two’s complement representation of +67 and -67. Your answers should be 8 bits long.
10. Carry out the indicated base conversions:
a) 548 to base 5
b) 3124 to base 7
c) 5206 to base 7
d) 122123 to base 9
11. If processor A has the higher clock rate than processor B, and processor A also has the higher MIPS rating than processor B, describe whether processor A would always execute faster than processor B. Assume that there are two implementations of same instruction set architecture. Machine A has the clock cycle time of 20ns and the effective CPI of 1.5 for some program, and machine B has the clock cycle time of 15ns and an effective CPI of 1.0 for the same program. Which machine is faster for this program, and by how much?
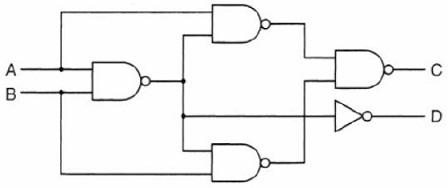
12. What does this circuit do?