problem1. Describe what you understand by Nyquist Capacity Theorem?
problem2. Assume we wish to transmit at the rate of 64 kbps over a 4 kHz noisy but error-free channel. What is minimum SNR in dB required to achieve this?
problem3. How is the rate improved when we double the bandwidth?
problem4. How is the rate enhanced when we double S/N?
problem5. Now assume that the above uses QPSK modulation becomes error-prone, what is the minimum signal power that is required to sustain the data rate of 64 kbps with a BER of 10-5 at 25 degrees Celsius?
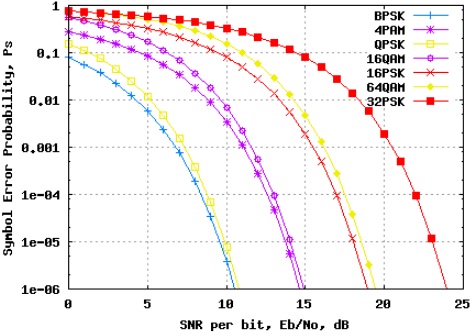
problem6. “Pulse Code Modulation (PCM), as used in the telephony, samples a signal at 8 kHz using 256 quantization levels”.
i) Outline how this scheme works with the assist of sketches and, by reference to the Nyquist’s Sampling Theorem, describe how the sampling rate was chosen.
ii) Compute the SNR in dB for the quantization error of this PCM setup.
iii) Compute the data rate achievable.
problem7. Give three merits which digital transmission has over analogue transmission.
problem8. describe three types of communication impairments which you are familiar with and, with reference to a standard communication model, state where the above-mentioned impairments usually occur.