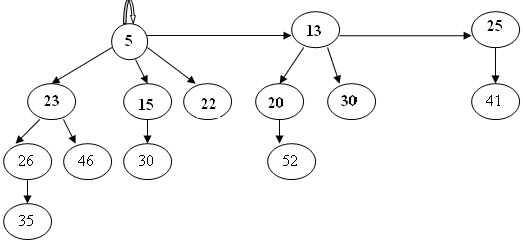
problem 1)a) Extract the minimum from the following Fibonacci Heap. (Indicate all the steps involved in this process)
b) Describe the method of representing the disjoint sets in the memory.
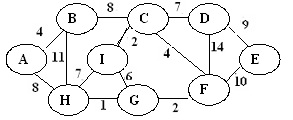
problem 2)a) Find the Minimum spanning Tree by applying Prim’s Algorithm on the following undirected graph. Indicate all the steps involved in this procedure.
b) Describe the concept of Directed acyclic graph to find shortest paths tree.
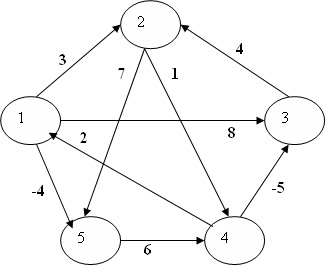
problem 3)a) Determine all pairs shortest paths for the following directed graph
b) Define the terms
(i) Predecessor matrix
(ii) Predecessor sub graph
(iii) flow network
(iv) Maximum flow network problem