problem 1) Describe major and minor elements of Object Model with suitable ex.
problem 2)a) Briefly describe various types of behavioural diagrams.
b) What are tagged values and constraints in UML? Describe with exs.
problem 2)a) What is an association relationship? Describe with exs navigation, visibility, qualification and interface specifier in the context of association relationship.
b) describe the class diagram shown below. Identify the classes and their associations.
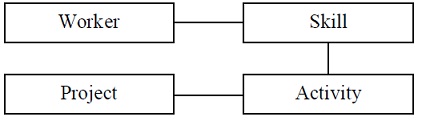
Update the diagram stepwise to demonstrate the class diagram in each case.
i) When a worker has a skill, the years of experience is maintained for the relationship.
ii) A worker may have another worker as the manager, and a worker who is a manager should manage five or more workers. Given a manager, you can find out whom she manages, but given a worker, you are unable to find out who his manager is.
iii) A worker is not simply related with set of skills, but a worker has skills. Specifically, a worker should have three or more skills, and any number of workers may have the similar skill.
iv) A project is not simply associated with set of activities, but a project contains activities. Specifically, a project should have one or more activities, and an activity must belong only to one project.
v) Projects and activities are specific types of work.