Q1. Create a binary tree whose following traversals are shown below:
In-order: DFEIHBAJCNOMK
Post-order: FIHEDBJONMKCA
Q2. Define the connected components of a Graph. For the graph shown below provide the adjacency list.
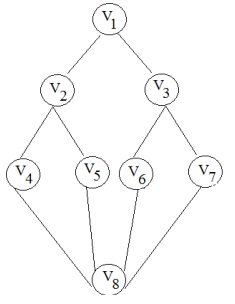
prepare down the BFS algorithm and traverse it starting from the vertex v6 showing different phases. How the connected components of a graph can be recognized?
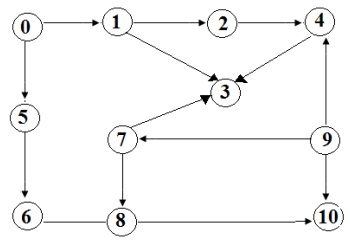
Q3. Find out the BFS Topological sorting of the graph shown below.