problem1)
Evaluate 0xF00 + 0x100
Express answer in hex notation.
problem2)
Assume integer 0x41FF is stored at word address 12 in a 32-bit little endian machine. What is a value in each byte location?
address 12 13 14 15
value
problem3)
Assume integer 0x41FF is stored at word address 12 in a 32-bit big endian machine. What is the value in each byte location?
address 12 13 14 15
value
problem4)
Assume integer -123 is stored at word address 12 in a 32-bit little endian machine in two’s complement format. What is the value in each byte location?
address 12 13 14 15
value
problem5)
Assume that x and –x are 8-bit integers represented in two’s complement format. Does x≥0 always implies -x≤0. If not, give a counter-ex.
problem6)
Assume that x and –x are 8-bit integers represented in two’s complement format. Does x≤0 always implies -x≥0. If not, give a counter-ex.
problem7)
A 2n-to-1 multiplexer, with n control bits and 2n input lines could be used to implement any binary function with (n+1) input variable. Assume you have following 4-to-1 (4 way) multiplexer.
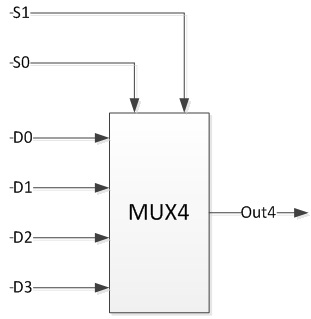
How could you connect the input lines D0, D1, D2, D3 above so that mux4 above implement the majority function M(s0, s1, s2)?
Hint: Each input line could be connected to either 0, 1, s2 or (s2) ¯. M(s0, s1, s2) = 1 if two or more input lines are of bit value ‘1’. Otherwise, M(s0, s1, s2) = 0.
problem8)
Consider following un-pipelined computation system. The computation in a combinational logic takes 400 ps to complete and storing the result to register takes 20ps. What is the throughput of the system? What is the delay of the system?
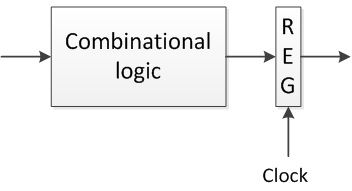
problem9)
Assume the computational logic in above block could be partitioned into k pipeline stages, each having a delay of 400/k ps. If k = 4, what is a throughput of the system and what is the delay of the system? If k approaches infinity, what is the throughput of the system and what is the delay of the system?