problem 1:
Illustrate the following data structures:
(a) List
(b) Stack
(c) Queues
Note: your explanation must comprise the definition, operations and instances.
problem 2:
Using insertion sort arrange the following numbers in ascending order. Exhibit each step and intermediate results. prepare algorithm.
10 2 3 4 11 9 8 5 12 1 6 7 0 -1 20
problem 3:
Make a binary tree for the following numbers supposing that a number greater than the node (starting from the root) goes to the left else it goes to the right.
15, 23, 7, 27, 11, 3, 28, 9, 13, 14, 12, 8, 10, 25, 24, 26, 30, 29, 1, 5, 6, 2, 0, 4, 19, 17, 16, 20, 18, 21, 22.
problem 4:
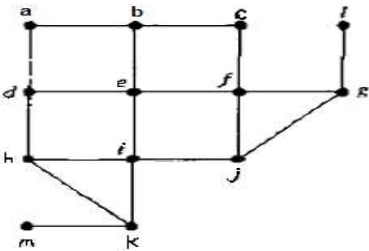
(a) State a tree and list its properties.
(b) By showing all your workings, draw the spanning tree for following graph based on Breadth-First-Search algorithm. Choose e as the root node.
(c) prepare an algorithm to carry out matrix multiplication.