Assignment
Exercise 1
Convert each of the following numbers to 8-bit signed magnitude, 8-bit one's complement and 8-bit two's complement. Report your answers in binary.
a. (-97)10
8-bit signed magnitude 8-bit one's complement 8-bit two's complement
b. (-47)10
8-bit signed magnitude 8-bit one's complement 8-bit two's complement
c. (-127)10
8-bit signed magnitude 8-bit one's complement 8-bit two's complement
d. 12610
8-bit signed magnitude 8-bit one's complement 8-bit two's complement
Exercise 2
Convert the following 16-bit two's complement numbers in hexadecimal representation to decimal.
a. AC2416
b. 64A216 c. 5D1716
d. FFFF16
Find the decimal equivalents for the following 8-bit two's complement numbers.
a. 0010 0100 Decimal Equivalent
b. 1010 1001 Decimal Equivalent
c. 1100 0011 Decimal Equivalent
d. 0101 0101 Decimal Equivalent
Exercise 4
Perform two's complement addition on the following pairs of numbers. In each case, indicate the value of the status bits after the addition. Assume NZVC=0000 prior to the addition.
a. 1000 0010 + 1000 0010 = NZVC=
b. 1010 1001 + 0110 1100= NZVC=
c. 1001 1111 + 1111 1110= NZVC=
d. 0111 1010 + 0110 0110= NZVC=
Exercise 5
Using the PEP/8 instruction, 72004A, answer the following questions. What is the instruction in binary?
Starting from the left, what do bits 6 - 8 represent? (be specific) For this instruction, what register will be used?
Explain what is stored in mem[004A]?
The following is in single-precision IEEE 754 format, 1 01111111 10110011001100110011010.
What is the sign bit?
Does the sign bit represent a positive or negative number?
What is the bias used in IEEE 754 single-precision format?
As shown above, what is the exponent in binary?
What is the exponent after the bias is removed? (In decimal)
As shown above, what is the significand in binary?
Explain why it is possible for error to be introduced when converting a decimal number to IEEE 754 format.
Exercise 7
Using the PEP/8 instruction, D11AA3, and the following table, answer the following questions.
|
|
Accumulator
|
Index Register
|
Mem[1AA3]
|
Mem[1AA5]
|
Mem[1AA7]
|
NZVC
|
|
Content
|
2A34
|
FF32
|
3AF0
|
2AFF
|
1AFF
|
0000
|
Content before instruction.
What is the instruction?
What is the register?
What is the addressing mode?
What is the content of the accumulator after the instruction is executed, (hex)?
What is the content of the index register after the instruction is executed, (binary)?
What is the content of mem[1AA3] after the instruction is executed, (hex)?
What is the content of mem[1AA5], (binary)?
What is the content of mem[1AA7], (hex)?
What is the RTL specification for this instruction?
What is the value of the NZVC bit after execution?
The following is in Pep/8 assembly language.
LDX 8, i
ORX 0x0030, i
STBYTEX num, d CHARO num, d STOP
num: .BYTE 0
.END
What is the output of this program?
What is ORX doing?
Why is the ORX instruction required?
What is the hexadecimal object code that is suitable for PEP/8. (Include all code necessary for the object code to run on the PEP/8. Use PEP/8 to check your work)
Exercise 9
The following is in Pep/8 assembly language.
DECO 'X', i CHARO '\n',i DECO 0xFFE3, i CHARO '\n',i CHARO 0x003D, i STOP
.END
What is the output of DECO ‘X', i?
What is the output of DECO 0xFFE3, i?
What is the output of CHARO 003D, i?
What is the hexadecimal object code that is suitable for PEP/8. (Include all code necessary for the object code to run on the PEP/8. Use PEP/8 to check your work)
Draw the runtime stack for the following C++ program. (Show any global variables and include main in the runtime stack)
Use
retAddr for the return address retVal for the return value NA not used
#include using namespace std; int ounces;
void size(int& ou, int lbs) { ou = lbs*16;
}
int main() {
int lbs;
cout << "Enter number of pounds"; cin >> lbs;
size(ounces, lbs);
cout <<"You have " << ounces << "ounces"; return 0;
}
Draw the call tree, as in Figure 2.30, for the function binCoeff of Figure 2.28 for the call statement from the main program: (e) binCoeff (4, 2)
Part 1) Draw the call tree for the call statement from the main program. (See Fig 2.30 for an example)
Part 2) How many times is the function called?
Part 3) What is the maximum number of stack frames on the run-time stack during the execution, including main).
Part 4) The sequence of calls and returns for the program. (See page 66 below Fig 2.30)
Exercise 12
The Fibonacci sequence is 0 1 1 2 3 5 8 13 21...
Each Fibonacci number is the sum of the preceding two Fibonacci numbers. The sequence starts with the first two Fibonacci numbers, and is defined recursively as:
fib(0) = 0
fib(1) = 1
fib(n) = fib(n-1) + fib(n-2) for n > 1
The C++ program that computes the Fibonacci number is as follows: #include
using namespace std; int fib (int n) {
if (n == 0) { return 0;
}
else if (n == 1) { return 1;
}
else {
return fib (n - 1) + fib (n - 2);
}
}
int main () { int num;
cout << "Which Fibonacci number? "; cin >> num;
cout << "The number is " << fib (num) << endl; return 0;
}
Part 1) Draw the call tree for the Fibonacci number fib(5)
Part 2) How many time is fib called?
Part 3) What is the maximum number of stack frames allocated on the run-time stack? (Do not include the main stack.)
Exercise 13
The object code for Figure 6.14 has a CPA at 000C to test the value of j. Because the program branches to that instruction from the bottom of the loop, why doesn't the compiler generate a LDA j,d at that point before CPA.
Exercise 14
Explain the difference in the memory model between global and local variables. How are each allocated and accessed in PEP/8?
Exercise 15
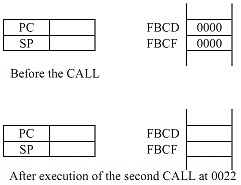
Draw the values just before and just after the CALL at 0022.