Assignment: GA and Stuck at Fault
1. Introduction to Evolvable Hardware
1a) Write 10 lines (or less) of high-level pseudocode to identify the flow of operations in a traditional implementation of a GA (i.e. sometimes called a Generational GA) as we have identified thus far in class. Please put your comments to explain each comments.
For example:
%this is a function call to activate genetic algorithm
Procedure Rudimentary_GA {
............
}
1b) What undesirable effect may occur during execution of an EHW strategy if the mutation rate is excessive, i.e. the probability of mutation is set to a value that is too large? What undesirable effect may occur if the mutation rate is exactly zero?
1c) Explain the distinction between a LUT and a CLB within the FPGA reconfigurable fabric.
1d) Specify TRUE or FALSE for the statement:
"A Genetic Algorithm can be relied upon to obtain a globally optimal solution assuming that it is allowed to execute for a very large number of generations."
Justify your answer with a concise explanation. Here the phrase "globally optimal solution" refers to the evolution of at least one instance of an individual which has the maximal fitness that can possibly exist for the application domain, i.e. in the case of EHW this would be a completely correct logic circuit.
1e) What is an advantage of a strategy to increase reliability that is based on a Refurbishment strategy rather than Redundancy? Alternatively, what is an advantage of Redundancy over Refurbishment?
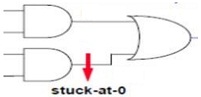
2. Please define input bits to test given fault. Please specify what observation at the output is?