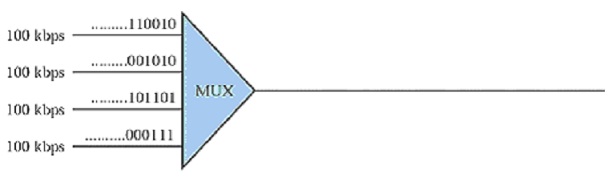
problem 1: A multiplexer combines four 100-Kbps channels using a time slot of 4 bits (see figure below). Each Frame has the size of 16 bits.
a) Show the output with the four inputs as shown in the figure below.
[Note: only show the output from the visual diagram illustrated]
b) What is the frame rate?
c) What is the frame duration?
problem 2:
i) Assume that frames are 1250 bytes long comprising 25 bytes of overhead. Also suppose that ACK frames are 25 bytes long.
a) Compute the efficiency of stop-and-wait ARQ in a system that transmits at R = 1 Mbps and reaction time 2(Tprop + Tproc) of the following: 1ms, 10ms, 100ms and 1 second.
b) Repeat if R = 1Gbps.
ii) Please discuss what options does an ARQ protocol have when it detects a frame with the errors?
iii) In a Stop-and-Wait ARQ system, the bandwidth of the line is 1 Mbps and 1 bit takes 20 ms to make a round trip.
a) What is the bandwidth-delay product?
b) If the system data frames are 1000 bits in length, find out the utilization percentage of the link?
c) Find out the utilization percentage of the link if the link uses Go-Back-N ARQ with a 15-frame sequence?
problem 3:
i) Consider a system by using flooding with hop counter. Assume that the hop counter is originally set to the ‘diameter’ (number of hops in the longest path without traversing any node twice) of the network. When the hop count reaches zero, the packet is discarded apart from at its destination.
Does this always make sure that a packet will reach its destination if there at least one functioning path (to the destination) that may exist? Why or why not?
[Suppose that a packet will not be dropped unless its hop count goes to zero]
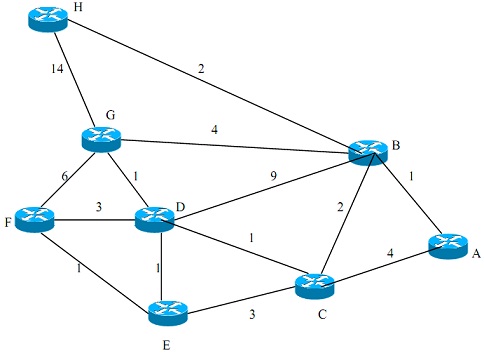
ii) Consider the network shown in figure below. Using Dijkstra’s algorithm and showing your work by using tables.
a) find out the shortest paths from A to all network nodes.
b) find out the shortest paths from B to all network nodes.
problem 4:
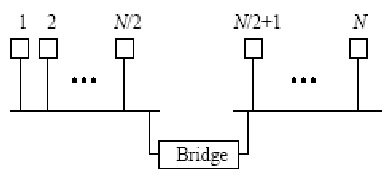
i) Assume that N stations are connected to an extended Ethernet LAN, as shown in figure below, operating at the rate of 10 Mbps. Suppose that the efficiency of each Ethernet is 80 percent. Also suppose that each station transmits frames at the average rate of R bps, and each frame is equally likely to be destined to any station (including to itself).
a) What is the maximum number of stations, N, that can be supported if R is equivalent to 100 kbps?
b) If the bridge is replaced with a repeater, what is the maximum number of stations that can be supported? (Suppose that the efficiency of the whole Ethernet is still 80 percent.)
problem 5:
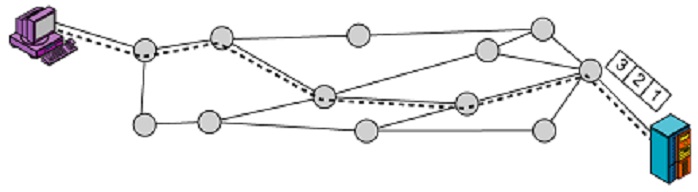
i) Assume there are exactly five packet switches (figure shown below) between a sending host and a receiving host connected by a virtual circuit line (shown as dotted line in figure below). The transmission rates between the different network elements are as follows:
Between sending host and the 1st switch the rate is 2R1;
Between the 1st and the 2nd switch the rate is 3R2;
Between the 2nd and the 3rd switch the rate is R3.
Between the 3rd and the 4th switch the rate is 3R2;
Between the 4th and the 5th switch the rate is R1;
Between the 5th and the receiving host the rate is R1;
Find out the total end-to-end delay to send a packet of length 2L?
ii) Consider an application which transmits data at a steady rate (for illustration, the sender generates an N-bit unit of data every k time units, where k is small and fixed). Also, when such an application begins, it will continue running for a relatively long period of time. Answer the given problems briefly justifying your answer:
a) Would a packet-switched or circuit-switched network be more suitable for the application? Why?
b) Assume that a packet-switched network is used and the only traffic in this network comes from such applications as describeed above. Furthermore, assume that the sum of the application data rates is less than the capacities of each and every link. Is some form of congestion control required? Why?
iii) Recall that ATM uses 53-byte packets consisting of five header bytes and 48 payload bytes. 53 bytes is unusually small for fixed-length packets; most networking protocols (IP, Ethernet, Frame Relay and so on) use packets that are, on average, significantly larger. One of the drawbacks of a small packet size is that a large fraction of link bandwidth is consumed by overhead bytes; in case of ATM, around 10% of the bandwidth is ‘wasted’ by the ATM header. In this problem we investigate why such a small packet size was selected.
a) Consider sending a digitally encoded voice source over ATM. Assume that the source is encoded at a constant rate of 64 Kbps. Assume each cell is completely filled before the source sends the cell into the network. The time needed to fill a cell is the packetization delay in milliseconds. In terms of L (bytes), find out the packetization delay in milliseconds.
b) Packetization delays greater than 20 msec can cause a noticeable and unpleasant echo. Find out the packetization delay for
i) L = 1,500 bytes (roughly corresponding to a maximum-sized Ethernet packet) and for:
ii) L = 53 (corresponding to an ATM cell).
c) Compute the transmission delay at a single ATM switch for a link rate of: R = 155 Mbps for:
i) L = 1500 bytes
ii) L = 53 bytes.
d) Comment on the advantages of using a small ATM cell.