1. Develop the function reachable. It consumes a node in a simple graph. Its effect is to place true into the visited fields of all those nodes that are reachable from the given node and to ensure that the visited fields of all other nodes are false.
2. Develop make-simple-graph, a function that manages the state of a locally defined graph. The function accepts a simple graph in the form of lists of pairs of symbols: (list of (list symbol symbol)). It supports four services:
1. adding nodes that are connected to already existing nodes (by name);
2. changing the connection of a node (by name);
3. determining whether a route between two nodes exists;
4. and removing nodes that are not reachable from some given node.
Hint: Instead of using a list, the manager should use a node sequence, which is analogous to the hand structure from section 41.3. A node sequence relies on the following structure:
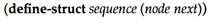
A sequence is similar to a list, but it supports structure mutations.