Assignment -
This is an individual coursework and must be completed independently.
Learning outcomes addressed: This assignment aims to assess the following learning outcomes:
1. Demonstrate knowledge and understanding of the theory and practice of modern digital techniques for the capture, processing and storage of visual data.
2. Critically analyse legal and ethical issues in computer vision as well as current technologies for security.
3. Apply and critically evaluate appropriate machine learning techniques to solve problems in computer vision.
Assignment Tasks -
Part 1-
Section A - Give a brief description of the image and video watermarking technology and discuss the different types of watermarking systems.
Explain how the watermarking technology can be used to solve legal and ethical issues in the acquisition, use and distribution of digital images and videos. Ensure you explicitly mention in your discussion the type of watermarking and its corresponding application.
No more than 300 words each.
Section B - You are provided with a test image saved as TIF file named 'peppers.tif'. For the purpose of image copyright protection, you are required in this section to implement a one-bit watermarking system in the wavelet domain and a similar watermarking system in the DCT domain as follows:
Wavelet domain watermarking:
Embedding: The input image is wavelet transformed with two levels of decomposition using the Haar wavelet. The second level sub-bands H2, D2 and V2 are used to hold three watermarks w1, w2, and w3 respectively (H stands for Horizontal, V for vertical, and D for Diagonal). These watermarks are of size (128 x 128) each and are saved in a MAT file named 'watermark.mat'. The embedding rule is additive with a watermark strength α =1.5. For instance, the ith wavelet coefficient in H2 is updated as
Y'(i) = Y(i) + α w1 (i)
where Y'(i) is the watermarked coefficient in H2. Y(i) is the original coefficient in H2. Once the coefficients are updated, the inverse wavelet transform is performed to obtain the watermarked image. This programme should produce the watermarked image in a TIF file.
Detection: This programme verifies the presence of the watermarks w1, w2, and w3 in the previously saved picture. First, two levels of wavelet decomposition are performed as before. Then, three similar watermark detectors are used for detecting w1, w2, and w3 that are stored in 'watermark.mat'.
Hints:
a- For the insertion of the watermark (Embedding), you may create a function which has two arguments (set of coefficients, watermark) and outputs the set of watermarked coefficients. Then, this function can be called in the main Embedding programme three times for the insertion of w1, w2, and w3, respectively. As for the detection, you may also need to create a function which has two arguments (set of coefficients, candidate watermark) and outputs a binary decision (1 if watermark exists, 0 otherwise). Once the function is created, it can be called in the main detection programme three times with different parameters.
b- You may convert a matrix into a column vector (or into a row vector) to perform the insertion and detection of the watermark. The syntax in matlab to convert a matrix A of M rows and N columns into a column vector is column_vector=A(:);
The inverse process (conversion from column vector into matrix) can be obtained by the following syntax Reconstructed_matrix=reshape(column_vector,M,N);
DCT domain watermarking:
Embedding: The input image is DCT-transformed. Three square regions are selected from the transformed image to hold w1, w2 and w3 (see figure) using the same multiplicative rule as before. Then, the inverse DCT is applied to get the watermarked image. This programme should output the watermarked image in a TIF file.
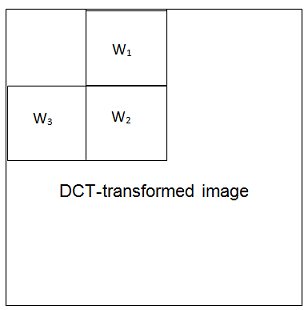
Detection: This programme verifies the presence of the watermarks w1, w2, and w3 in the previously saved picture. First, the DCT is applied on the watermarked image. Then, three similar watermark detectors as described earlier are used for detecting w1, w2, and w3 which are stored in 'watermark.mat'.
Section C - Explain how experiments can be conducted to assess the performance of the watermarking systems described above. No Matlab codes are required for this question.
No more than 150 words.
Part 2 -
Section A - Explain how you can distinguish compressed format from non compressed formats that are used to store colour and grey scale pictures/videos. Examples may help.
No more than 400 words.
Section B - Discuss the different types of machine learning systems. A diagram showing the classification of machine learning systems may help.
No more than 300 words.
Section C - The implementation of a logo detection system using an Artificial Neural Network is given in Matlab. The Matlab function 'getFeatureVector.m' extracts 11 features from any input colour or greyscale image by using the grey scale plane only in the Discrete Wavelet Transform (DWT) domain. There are two types of training images: logo and non logo images which are stored in two folders 'Logo' and 'Non_logo', respectively. The extracted features for both logo and non logo images will be used to train the classifier with 'ANN_training.m'. Once the classifier is trained, it can be evaluated on test images stored in a folder 'Test_logo'. Note that the first 30 test images contain a logo whereas the remaining ones are non-logo images. This is implemented via the Matlab code 'ANN_testing.m' where the default image is '1.jpg'. The idea is to verify the presence of a logo in each test image using the trained classifier. If a logo image is detected, the classifier will display a message 'Logo'. Otherwise, the message 'Non logo' is displayed.
1. Based on the existing Matlab codes ('ANN_training.m' and 'ANN_testing.m'), create new codes that implement the linear perceptron, the Naive Bayes classifier, and a classification tree. You should submit only the part of codes which are different from the current ones.
2. The false positive rate (FPR) is defined as the proportion of falsely classifying a non logo image as 'Logo'. The false negative rate (FNR) is the proportion of misclassifying logo images. For instance, if the system is applied on 30 non logo images and there are 2 incorrect classifications (i.e. classified as Logo), FPR=2/30. If the system shows 5 incorrect classifications on 30 logo images, FNR=5/30. Run the Matlab codes on all test images and complete the following table [6].
|
|
Linear Perceptron
|
ANN
|
Decision Tree
|
Naive Bayes
|
|
FPR
|
|
|
|
|
|
FNR
|
|
|
|
|
|
Error = (FPR+FNR)/2
|
|
|
|
|
3. Analyse and interpret the results.
No more than 500 words.
4. Explain how the performance of the logo detection system can be improved. No more than 500 words.
Attachment:- Assignment Files.rar