Assignent: EA Management Information System
1. A college registrar keeps the registration records on students and their courses to take in the spread sheet with the column headings: LastName, FirstName, Phone, CourseTitle, CourseDate, CourseFee, and AmountPaid.
a. The registrar can keep the records in this way on the spreadsheet, but they will soon find inconveniences in handling the pets information. What kind of problems or issues may occur if they keep recording in this way? Think in terms of data entery, updating data, or deleting data.
b. To avoid the above problems, the registration records may need to be kept in separate "tables" in the Microsoft Access terms. How the tables should be set up to keep the registration information? You can write the table name and its contents such as TableName(fieldname1, fieldname2, etc).
c. For the tables you set up in b, assign or add appropriate primary keys and foreign keys for each table. Some table wouldn't need a foreign key. The primary key should be underlined, and foreign key in italic such as TableName(primarykeyname, fieldname1, fieldname2, foreignkeyname, etc).
[Chapter 7Telecommunications]
2. For the given Figure 7-3, explain how the original message can reach to the destination as follows.
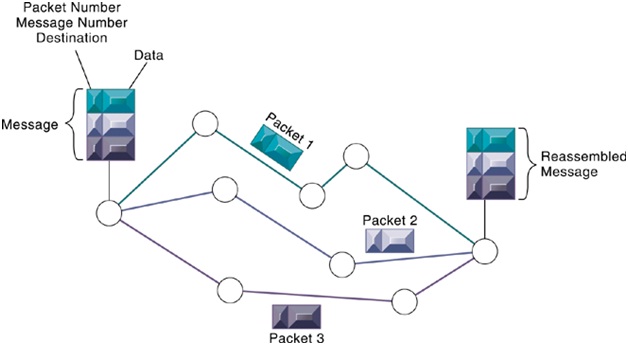
Figure 7-3 Packet Switched Network
a. Explain why the original message is divided into packets.
b. Describe how the packets can be composed to make the original message.
c. Explain why some packets travel different route on the way to the destination.
d. Some cases, a packet can be lost on the way to the destination. If the destination computer finds a packet is lost, what prototcol will correct situation? How does it recover the lost packet?
[Chapter 8Securing Information System]
3. Describe the processes how the Digital Certificate is working to confirm a person's indentity involved in the financial transaction. How can the digital certificate processes be safe guarded?
[Chapter 11Managing Knowledge]
4. How the Fuzzy Logic for Temparature Control (Figure 11-8) would work better than the ON-OFF switching method in controlling the thermostat?
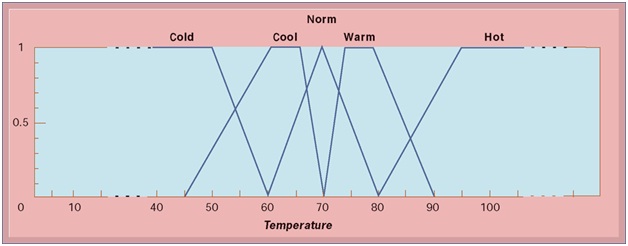
FIGURE 11-8
[Chapter 12Enhancing Decision Making]
[Chapter 13Building Information System]
[Chapter 14Managing Projects]
5. The US Army has planned to develop an intelligent warfighting capability by providing continuous wireless communication capability to update the current battle situtaion and to deliver directions to the warfighters in realtime. In the consideration of its importance, the Army started as a huge sized program that contains numerous projects from tank redesign, communication equipment development, logistics system, to training all at once. The necessary technologies of the combined wireless communications are yet to be developed. Software development was not easy to define.
a. In this case, what kind of problems or risks would arise as the program proceeds?
b. As the whole program is not progressing as expected, the Army determined to cancel the Program. If the program is stopped, all previous efforts might be lost. To salvage the previous works and continuously pursue the development goal, the Army plans to contnue in a much smaller scale project. If you are in the project management team, describe how the team would develop the project management strategies.